

Shortage of cybersecurity talent
Security professionals are expensive and hard to retain
New compliance and regulation requirements
Undocumented processes in the event of an attack or breach
Security technology is expensive and hard to maintain
Technology alone can't deter motivated attackers
Lack of visibility across the enterprise
Difficulty managing multiple tools and investigating all alerts
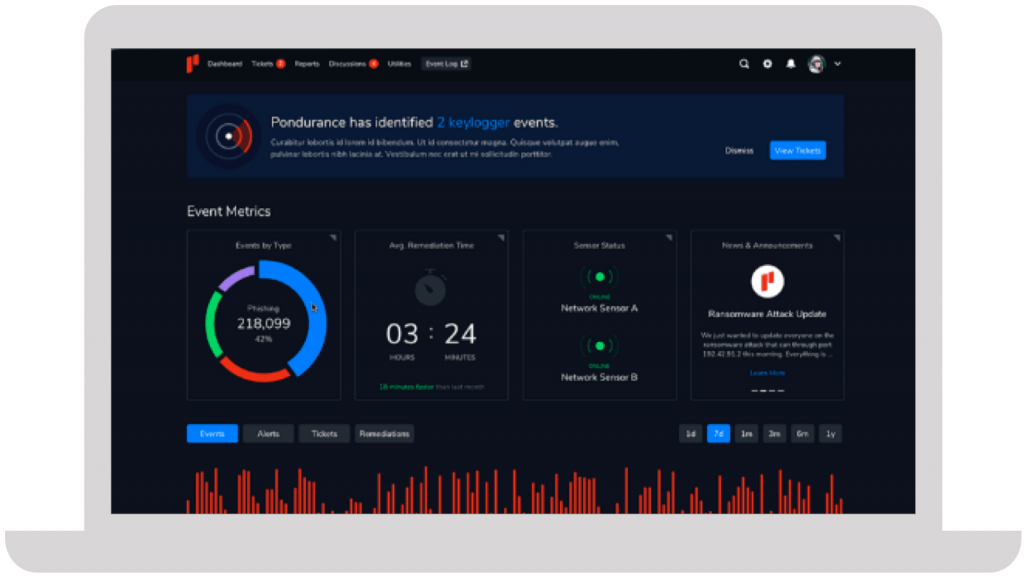
We take a personalized approach to developing your cybersecurity program. Instead of an all-or-nothing approach like other MDR providers, Pondurance lets you pay for what you need, without sacrificing the visibility and transparency you want.
The number of data breaches continues to escalate, putting small businesses on high alert. Nowadays, any information that a business finds valuable is monetizable and a potential target for attack. Learn more in our eBook.
Your company has its own unique set of cyber risks. Though you can’t control the evolving cyber landscape, you can control your cybersecurity strategy. But what’s the best strategic approach to cybersecurity today? Learn more in our eBook.
Join us on-demand to discuss components of MDR and how to choose the right provider for your organization.







They immediately proved their value and earned our trust due to their immense expertise and guidance throughout the entire process.
Steve Long, CEO @ Hancock Health
In today’s interconnected world, where digital transformation is pervasive, businesses face an ever-expanding array of cybersecurity threats. From ransomware attacks to sophisticated phishing schemes, the cyber landscape is constantly evolving, presenting new challenges to organizations of all sizes. In such a dynamic environment, the role of cybersecurity companies like Pondurance becomes paramount in safeguarding businesses against cyber risks.
Pondurance, recognized as one of the top cybersecurity companies, offers a comprehensive suite of services designed to address the diverse needs of modern businesses. Central to Pondurance’s approach is its emphasis on informed security practices and proactive risk management. By conducting thorough cyber threat assessments and leveraging advanced threat intelligence, Pondurance equips businesses with the insights needed to anticipate and mitigate potential cyber threats.
Moreover, Pondurance understands that effective cybersecurity goes beyond technology—it requires a holistic approach that encompasses people, processes, and technology. That’s why Pondurance focuses not only on deploying cutting-edge security solutions but also on empowering organizations to build a culture of security awareness. Through training programs, workshops, and ongoing education initiatives, Pondurance helps organizations cultivate a workforce that is vigilant and prepared to defend against cyber threats.
Additionally, Pondurance recognizes the importance of compliance and regulatory requirements in today’s business environment. With an in-depth understanding of industry-specific regulations such as GDPR, HIPAA, and PCI DSS, Pondurance helps organizations navigate the complex landscape of compliance, ensuring that they meet regulatory standards while also bolstering their cybersecurity defenses.
By partnering with Pondurance, businesses can gain access to a team of seasoned cybersecurity professionals who are dedicated to helping them navigate the challenges of the digital age. Whether it’s implementing robust security protocols, conducting vulnerability assessments, or responding to cyber incidents, Pondurance offers the expertise and support needed to safeguard organizations against cyber threats effectively.
In conclusion, in a world where cyber threats are increasingly sophisticated and pervasive, cybersecurity companies like Pondurance play a crucial role in helping businesses mitigate risk and protect their sensitive data. Through a combination of advanced technology, strategic guidance, and a commitment to excellence, Pondurance empowers organizations to navigate the complexities of the cyber landscape with confidence, ensuring a secure and resilient digital future.
Cybersecurity advisory services are professional services that aim to protect the digital and physical assets of an organization from myriad cyber threats. They are crucial in today’s digital age where technologically advanced threats pose a serious challenge to companies of all sizes, particularly small to medium-sized businesses. These threats can wreak havoc on an organization’s operations, reputation, and bottom line.
In this realm of uncertainty and constant threats, organizations find solace in partnering with cybersecurity firms like Pondurance. Offering a host of cybersecurity consulting services, Pondurance is dedicated to protecting organizations against emerging cyber threats. They specialize in a risk-based consultative approach that recognizes the unique risks any given organization may face, which helps in delivering tailor-made cybersecurity solutions rather than generic one-size-fits-all tactics.
One of the prime offerings of Pondurance is its Virtual Chief Information Security Officer (vCISO) service. In an age where digital security roles are essential yet sometimes not affordable for small to mid-sized businesses, vCISO provides a cost-effective solution. This service presents businesses with access to a CISO who drives critical security initiatives and oversees security programs, without being a full-time, on-staff position. A vCISO brings to the table leadership, expertise, and a strategic perspective, optimizing the security infrastructure in alignment with the organization’s business objectives.
Pondurance serves as more than just a cybersecurity consultant; rather, it acts as a trusted cybersecurity advisor. Their cybersecurity advisory services extend beyond tackling immediate threats to providing ongoing cyber threat intelligence, security program management, crisis management, and incident response. These services are ingrained in Pondurance’s offerings with the prime target to enhance the organization’s cybersecurity posture in a dynamic threat landscape.
The collaboration with a cybersecurity organization like Pondurance benefits businesses in several ways. Firstly, it amplifies their protection against rising cyber threats. With seasoned specialists leading defense strategies, risks are identified and mitigated before they manifest into full-fledged attacks. Secondly, it brings an element of cost-effectiveness, as organizations can leverage top-tier security expertise and strategies without bearing the expense of a full-time internal security team. Lastly, having an advisor like Pondurance provides businesses with a sense of security, enabling them to focus more on their core functionalities and less on security concerns.
In a nutshell, cybersecurity advisory services, including those offered by Pondurance, provide businesses with the threefold benefit of high-level security, cost-efficiency, and peace of mind. They fill the security leadership gap, navigate the complex security landscape, and implement effective defense mechanisms. By integrating cybersecurity consulting and advisory services, organizations can ensure the robustness of their digital security and the continuity of their business operations amidst an ever-evolving digital threat landscape. These services prove to be of immense value, particularly for small to medium sized businesses, that are a prime target of cyber threats due to the perceived lack of adequate security measures.
In today’s digital landscape, businesses face ever-evolving cybersecurity threats that can jeopardize their operations and sensitive data. That’s where trusted cybersecurity companies step in, offering invaluable support in managing cyber risk and enhancing cyber threat assessment. One such top cybersecurity company is Pondurance, renowned for its expertise in informed security practices and threat intelligence.
Pondurance’s Virtual Chief Information Security Officer (vCISO) service stands out as a proactive cyber risk management strategy tailored to meet organizations’ diverse cybersecurity needs. By leveraging the expertise of a seasoned vCISO, businesses can bolster their security posture and mitigate potential impacts of data breaches and cyber threats.
At Pondurance, the role of a cybersecurity consultant extends beyond mere threat detection and response. It encompasses proactive vulnerability management, establishment of robust security protocols, and fostering a culture of security awareness within organizations. This comprehensive approach empowers security teams to stay ahead of emerging cybersecurity threats and safeguard their information systems effectively.
By partnering with Pondurance, small to medium-sized businesses gain access to industry-leading cybersecurity expertise that helps them navigate the complexities of cybersecurity with confidence. With a focus on risk assessments and tailored security solutions, Pondurance equips businesses to address potential threats and strengthen their defense against cyber adversaries.
The cybersecurity landscape is rife with challenges, from sophisticated cyber attacks to regulatory compliance requirements. Pondurance recognizes the importance of staying ahead of these challenges and offers specialized services such as cyber threat intelligence and incident response planning. By leveraging advanced threat intelligence capabilities, Pondurance helps organizations identify and mitigate emerging threats before they escalate into major incidents.
Moreover, Pondurance’s incident response planning ensures that organizations are well-prepared to handle data breaches and cyber incidents effectively. From developing incident response playbooks to conducting tabletop exercises, Pondurance assists organizations in building resilient cyber incident response capabilities.
In addition to proactive risk management, Pondurance emphasizes the importance of continuous security monitoring and assessment. Through its managed security services, Pondurance provides round-the-clock monitoring of networks and systems, enabling organizations to detect and respond to potential security incidents in real-time. This proactive approach helps organizations minimize the impact of cyber threats and maintain a strong security posture.
Furthermore, Pondurance offers comprehensive security assessments to help organizations identify and address security vulnerabilities across their IT infrastructure. By conducting thorough assessments of networks, applications, and endpoints, Pondurance helps organizations identify potential security gaps and develop remediation plans to strengthen their security defenses.
Overall, Pondurance’s holistic approach to cybersecurity encompasses proactive risk management, incident response planning, continuous security monitoring, and comprehensive security assessments. By partnering with Pondurance, organizations can enhance their cyber resilience and protect their sensitive data from evolving cyber threats.