

Shortage of cybersecurity talent
Security professionals are expensive and hard to retain
New compliance and regulation requirements
Undocumented processes in the event of an attack or breach
Security technology is expensive and hard to maintain
Technology alone can't deter motivated attackers
Lack of visibility across the enterprise
Difficulty managing multiple tools and investigating all alerts
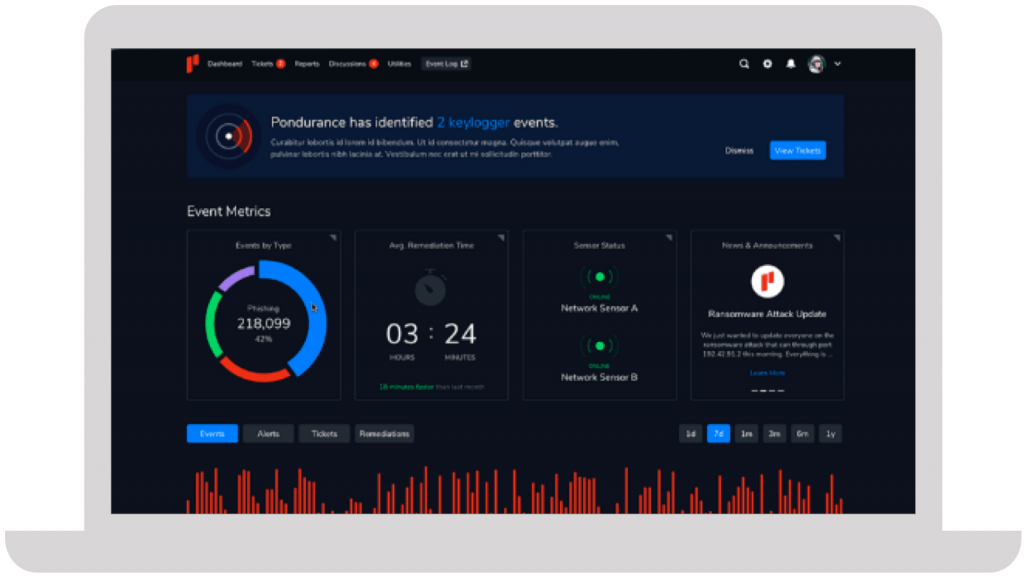
We take a personalized approach to developing your cybersecurity program. Instead of an all-or-nothing approach like other MDR providers, Pondurance lets you pay for what you need, without sacrificing the visibility and transparency you want.
The number of data breaches continues to escalate, putting small businesses on high alert. Nowadays, any information that a business finds valuable is monetizable and a potential target for attack. Learn more in our eBook.
Your company has its own unique set of cyber risks. Though you can’t control the evolving cyber landscape, you can control your cybersecurity strategy. But what’s the best strategic approach to cybersecurity today? Learn more in our eBook.
Join us on-demand to discuss components of MDR and how to choose the right provider for your organization.







They immediately proved their value and earned our trust due to their immense expertise and guidance throughout the entire process.
Steve Long, CEO @ Hancock Health
As more and more companies rely on technology to run their daily operations, the risk of cyber threats has grown exponentially. It is crucial for small business owners to understand the importance of cybersecurity in business and implement the best cybersecurity practices to protect their valuable data and customer information.
One major aspect to consider when discussing cybersecurity for small businesses is finding the best cybersecurity solutions tailored specifically for the needs of the organization. Small businesses often have limited resources, which can make it difficult for them to invest in robust security measures. Nevertheless, there are affordable and effective options available that cater specifically to the unique needs of smaller enterprises.
For example, some providers offer comprehensive packages that include firewalls, antivirus software, intrusion prevention systems, and encryption services – all designed with small businesses in mind. By selecting one of these packages, a small business owner can ensure they are taking the necessary steps toward protecting their company from potential cyber threats.
Another key factor in ensuring proper cybersecurity for a small business is educating employees on safe online practices. All staff members should be trained on how to recognize phishing emails, create strong passwords, and securely store sensitive information. Additionally, implementing clear policies regarding internet usage at work can also help minimize risks associated with employee behavior.
Small business cybersecurity must be taken seriously as even relatively minor breaches could result in significant consequences. To effectively protect against such threats, it’s vital for small businesses to identify affordable yet comprehensive solutions tailored specifically to their unique needs while fostering a culture of security through regular employee education and training sessions.
Cybersecurity risk assessments are a vital process that helps organizations identify, evaluate, and prioritize potential risks in their IT systems. The primary goal of a risk assessment is to minimize the likelihood of cyber attacks and the damage they may cause. By conducting a thorough cybersecurity risk assessment, businesses can develop an effective strategy for managing and mitigating security risks, thus reducing their overall exposure to cyber threats.
One essential component of a comprehensive cybersecurity risk assessment is threat hunting and response. Threat hunting involves proactively searching for evidence of malicious activity within an organization’s network, applications, and data storage systems. This process requires highly skilled professionals who are knowledgeable in various aspects of cybersecurity management.
Threat hunting greatly enhances an organization’s ability to detect and respond to cyber attacks before they cause significant damage. It also enables the continuous improvement of cybersecurity management practices by providing valuable insights into the latest tactics used by hackers and other malicious actors.
The dynamic nature of cyber threats means that organizations must constantly evolve their cybersecurity assessment processes to stay ahead of emerging risks. Implementing cutting-edge technologies, such as artificial intelligence (AI), machine learning (ML), and advanced analytics, can help organizations gain deeper insights into potential vulnerabilities and develop more robust defense strategies.
Implementing a holistic approach towards cybersecurity management necessitates embracing various practices like proactive threat hunting and response mechanisms alongside conducting regular cybersecurity assessments. A comprehensive cybersecurity risk assessment empowers organizations with valuable information on existing vulnerabilities, allowing them to take appropriate measures against looming threats effectively.
Cybersecurity is a crucial aspect for businesses of all sizes in today’s digital world, and small organizations are no exception. It is essential for small business owners to take measures to ensure the protection of their sensitive data and systems from cyber threats.
One important aspect of ensuring the safety of your small business is assessing the security measures taken by vendors you work with. A vendor cybersecurity checklist will help you evaluate potential partners based on their security policies and practices. The list should include:
* Assessment of network security
* Password management practices
* Use of encryption technologies
* Staff training on data protection protocols
* Any certifications or compliance with industry standards
Ensuring that your vendors adhere to stringent security measures will go a long way in safeguarding your own data. Understanding the fundamentals of cybersecurity is vital for small business owners as it empowers them with the knowledge necessary to make informed decisions regarding the protection of their digital assets. This means staying updated on emerging threats, understanding common attack methods used by hackers (such as phishing scams), learning about encryption technologies to protect sensitive information being sent over networks, creating strong passwords that are difficult to crack or guess, and instituting basic security protocols like regularly updating software programs with patches.
Cybersecurity best practices are not just applicable to large enterprises but should be integral aspects of every business operation regardless of size. Small businesses must prioritize the following:
* Implementing firewalls at network perimeters to protect internal systems from unauthorized access
* Using secure file transfer protocols when sharing sensitive information
* Deploying intrusion detection systems to monitor network activity
* Providing regular training sessions to employees on responsible online behavior
* Ensuring that all devices connected to company networks have up-to-date antivirus software installed
You need to regularly conduct risk assessments, develop a comprehensive incident response plan, and consistently monitor systems for signs of compromise or unauthorized access. Employing a layered defense strategy that addresses potential threats at multiple levels will further strengthen the security posture of the organization.
If you can only have just one takeaway from this article, let it be this: In today’s constantly changing digital landscape, the significance of cybersecurity risk assessment services cannot be emphasized enough. Using the right assessment tools is everything, literally! While cyber threats continue to evolve, it is only through risk assessment that these risks can be identified, evaluated, and ultimately managed. To conduct a thorough analysis of an organization’s security posture, most organizations employ MDR consultants as they are skilled enough to provide actionable insights that help mitigate live risks. MDR consultants also ensure that companies comply with industry standards and regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Remember, you can always get the top-of-the-line Pondurance services when you allow us to offer you our holistic MDR services in dealing with cybersecurity.
After assessing the potential cybersecurity risks in an organization, the next step is for organizations to develop a comprehensive cybersecurity risk management plan. This strategic document enables organizations to stay ahead of emerging threats while maintaining regulatory compliance. However, it has to be formally written so that the policies, processes, and controls necessary to protect an organization’s digital assets and sensitive information from cyber threats are ingrained into the organization’s strategic plans and operating procedures. The cybersecurity risk management plan should also be detailed and thus include fine details such as threat identification and prioritization approaches, incident response planning, risk mitigation strategies, employee training programs, and continuous monitoring activities.
Ultimately, effective cybersecurity risk management is vital for the long-term success of any business operating in today’s digital landscape. By adopting a robust cybersecurity risk management framework, prioritizing risks and controls, and measuring their progress through quantitative metrics, organizations can mitigate cyber threats more effectively and subsequently safeguard their critical assets. Moreover, even when they suffer from a cyber attack, organizations with a cybersecurity risk management plan can act swiftly to counteract the attack and reduce its potential impact. Therefore, as technology plays a central role in our everyday operations, it becomes more critical for organizations to actively manage cybersecurity risks. Contracting MDR consultants is undoubtedly one of the best ways to stay ahead of cybersecurity threats, and we dare say that at Pondurance, we are the best!
Incident response in the realm of cybersecurity is a crucial and highly specialized process that organizations must adopt to efficiently and effectively address security breaches, cyber-attacks, and other malicious activities. As businesses become more reliant on digital systems and networks, the need for a well-rounded cyber incident response plan grows exponentially. With an increasing number of threats emerging every day, it is essential for companies to be prepared with plans in place to minimize damages, protect valuable assets, and maintain customer trust.
A comprehensive cyber incident response plan consists of various elements aimed at identifying, containing, eradicating, and recovering from security threats. These steps not only mitigate risks but also ensure the continuity of business operations despite potential setbacks caused by cyber-attacks. The significance of cyber incident response becomes apparent when we consider the potentially disastrous consequences of data breaches and security compromises.
A well-executed response strategy can mean the difference between an organization’s survival or irrecoverable loss. For this reason, companies are advised to invest time and resources into developing robust incident response procedures that involve all stakeholders – including IT personnel, management teams, legal advisors, and public relations representatives – working collaboratively towards addressing incidents promptly and thoroughly.
In recent years, there has been a notable shift towards proactive approaches to managing cybersecurity incidents. This approach includes thorough risk assessments that identify vulnerabilities within an organization’s infrastructure before they can be exploited by attackers. Additionally, continuous monitoring capabilities are being employed to detect potential threats as soon as they arise. The combination of these strategies allows businesses to outpace hackers by staying ahead of their tactics and taking timely action whenever necessary.
As companies of all sizes face a growing number of cyber threats, it has become increasingly important for small businesses to have a mature cybersecurity posture. A cybersecurity consultant can help small businesses identify and address potential vulnerabilities in their systems, ensuring the safety and security of their valuable data. This service is essential for businesses that rely on technology for daily operations, such as e-commerce, customer relationship management, and data storage.
One of the primary services offered by a cybersecurity consultant, like Pondurance, is managed detection and response (MDR). An MDR consultant specializes in providing continuous monitoring and analysis of network traffic to detect and respond to threats in real time. By employing advanced threat intelligence techniques and utilizing cutting-edge tools, an MDR consultant can quickly identify any unusual activity or intrusion attempts before they lead to significant damage or loss.
Cybersecurity solutions for small businesses are tailored to the unique needs of each company. These solutions typically involve a mix of technology, processes, and people working together to protect sensitive information. Some examples include firewalls, anti-virus software, employee training programs on safe online practices, and strict access controls for sensitive data.
When choosing the best cybersecurity for small business operations, it’s crucial to consider factors such as budget constraints, industry-specific regulations, and the complexity of IT infrastructure. Small business cybersecurity consulting services can guide decision-makers through this process by providing expert advice on which solutions would be most effective at mitigating risks without breaking the bank.
Many small businesses may not have dedicated IT staff with expertise in cybersecurity matters; therefore, outsourcing these responsibilities to cybersecurity services for small business providers is a practical approach. These external experts bring knowledge from various industries with diverse threat landscapes enabling them to implement robust defenses catered specifically towards small businesses’ needs.
Investing in small business cybersecurity consulting is crucial in today’s fast-paced digital environment where cyber threats are constantly evolving. By partnering with a skilled cybersecurity consultant, like Pondurance, small businesses can access MDR expertise and receive customized cybersecurity solutions designed to fit their unique requirements. These services not only help protect the organization from potential risks but also enhance overall business resilience, ensuring long-term success in an increasingly interconnected world.