Our privacy policy is located here.
In 2021, organizations experienced a 68% increase in breaches, the highest number of breaches ever reported in a year, according to Identity Theft Resource Center. And in the first quarter of 2022, the number of publicly reported data breaches was up 14% over 2021. The expanded attack surface has contributed to the increase in data breaches. Today’s cyberattackers are no longer looking to steal only sensitive customer data such as Social Security numbers and credit card information. Ransomware has redefined “monetizable data.” Now, any information that a business finds valuable, such as maintenance records on a fleet of trucks or a manufacturer’s third-party supplier information, is monetizable and a potential target for attack.
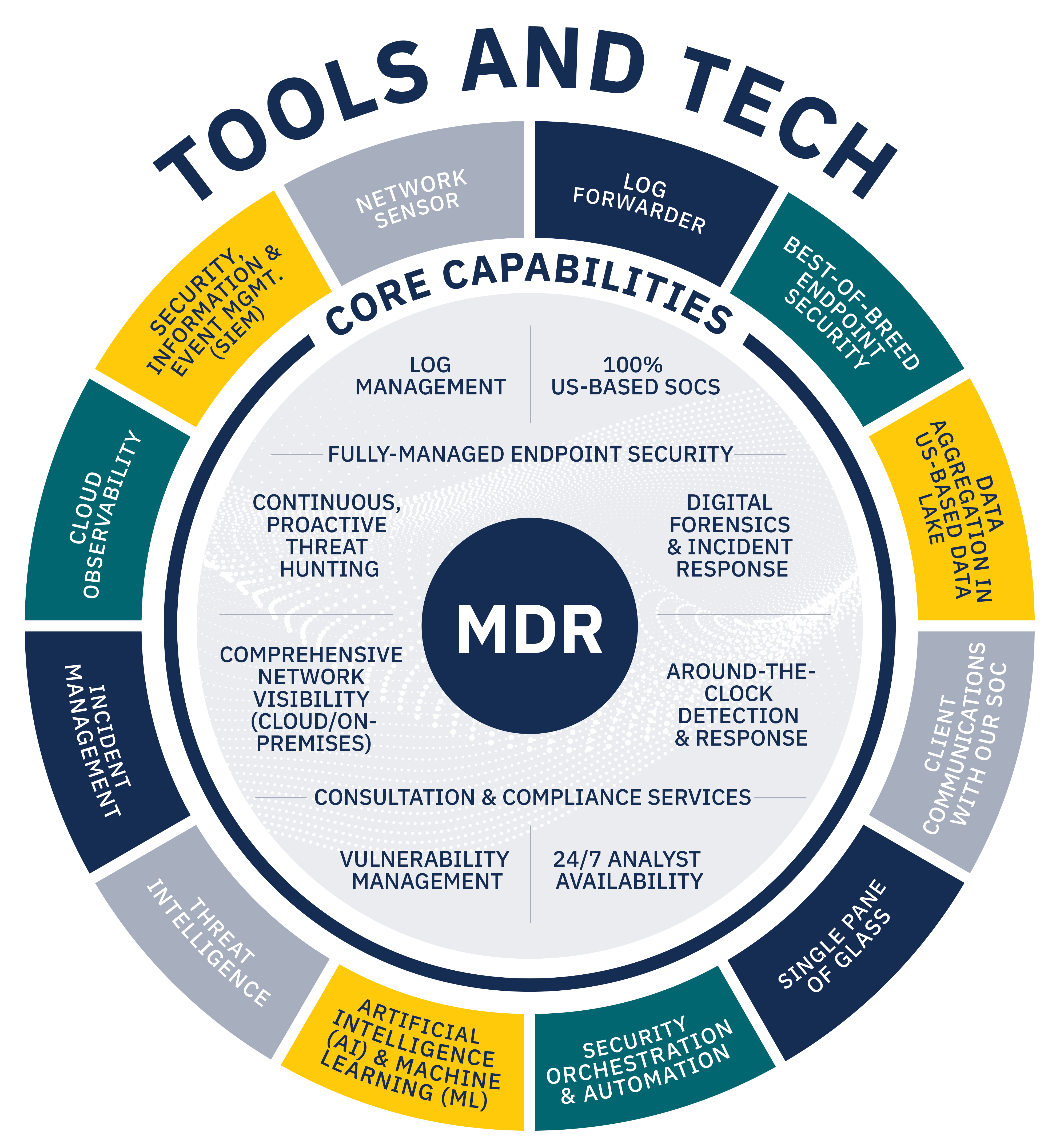
To protect such data, many organizations are turning to managed detection and response (MDR) services, a category of security solutions that offers the technology, process, and expertise needed to defend against the increasing threat of cyberattacks. Technological research and consulting firm Gartner projects that 50% of all organizations will use MDR services by 2025.† But not all MDR providers are created equal. Businesses looking for an MDR provider in the evolving cyber landscape are having to sort through the confusion to find the right MDR provider for their needs.
After reading this guide, you will have a better understanding of available MDR services and how those options may align with your needs. The guide covers:
- Exploring MDR’s history
- Simplifying the need for complex technology
- Fighting cyberattackers with human defenders
- Bringing the ‘R’ to MDR
- Customizing solutions for today and tomorrow
- Knowing compliance vs. cybersecurity
- Understanding your industry
- Tailoring to your needs and budget
† 2021 Gartner Market Guide for Managed Detection and Response Services, Gartner, October 2021.