Our privacy policy is located here.
Risk-Based Cybersecurity
with Managed Detection and Response and Pondurance Security Operations Center (SOC) Services
What is a Security Operations Center?
A SOC is the right collection of technologies and people–security analysts, threat hunters, threat intelligence and incident response experts—all working together to detect and respond to cyberthreats and reduce your risk.
"A SOC is a centralized function operating as first responders for attempted intrusions with responsibilities that include detection, analysis, investigation and response on a 24/7 basis.”
– Forrester Opportunity Snapshot: July 2022
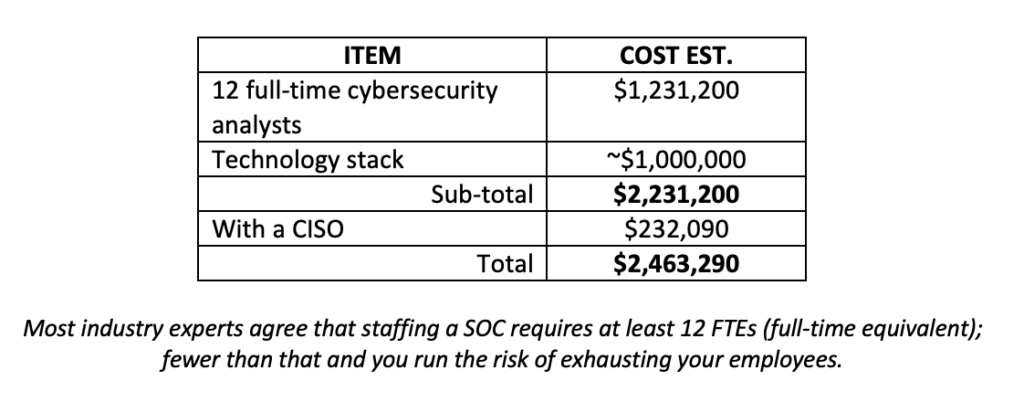
Building your Own SOC Vs. Outsourcing
Pondurance MDR and SOC Services
Gartner Says:
Pondurance Agrees:
See how Pondurance Aligns with what Gartner Recommends for MDR
Ready to Start the Conversation with a Pondurance Expert?
Get a risk assessment or request a demo today to get started!
SOC as a Service
SOC as a Service, or Security Operations Center as a Service, is an innovative approach to cyber security that provides organizations with both comprehensive security management and monitoring solutions. This service model helps businesses of all sizes stay ahead in the ever-evolving world of cyber threats while also maintaining the highest levels of security. Find out more about SOC in cyber security and learn about the benefits of partnering with a trusted provider like Pondurance.
A Security Operations Center (SOC) is a centralized facility responsible for actively monitoring, detecting, analyzing, and responding to cyber threats in real time. Equipped with advanced tools and technology, a SOC safeguards an organization’s digital assets against potential attacks. However, not all businesses have the resources or expertise to establish their own internal SOC. This is where SOC as a Service comes into play. Managed service providers offer SOC as a Service (SOCaaS), delivering effective security operations center capabilities on-demand without requiring clients to build their own infrastructure or train personnel. Overall, this would enable an organization to save on both time and costs.
In order to better understand SOC as a Service, let us take a look at a real world example:
Imagine that you run a medium-sized company. You have set up a Security Operations Center (SOC) to monitor your network and systems for any suspicious activities or potential security breaches. Your SOC is staffed around the clock by trained security analysts who use advanced tools and technologies to detect and respond to threats in real time. They analyze logs, monitor traffic, and investigate any anomalies that might indicate a cyber threat. Additionally, they collaborate with other teams in your organization to implement security measures in addition to ensuring compliance with industry regulations. The SOC serves as a critical line of defense, protecting your organization’s sensitive financial data and customer information from cyber attacks.
One of the key benefits of SOC as a Service is its scalability. As your business grows or faces new or unforseen challenges, SOC as a Service allows you to adapt your security measures without the major overhaul cost. Additionally, managed service providers possess specialized knowledge and experience in cybersecurity, making them well-equipped to respond proactively to emerging threats.
The increasing popularity of SOC as a Service is due to its effectiveness in providing robust protection against various forms of cyber attacks. With attackers worldwide employing sophisticated technologies such as artificial intelligence and machine learning, traditional methods alone are no longer enough for world-class security. By leveraging SOCaaS offerings from managed service providers, organizations have the ability implement cutting-edge defenses that keep pace with evolving threat landscapes.
To summarize, Security Operations Centers are crucial for protecting an organization’s digital assets from cyber threats. With the growing complexity of attacks and potential damages associated with data breaches, more businesses are turning to SOC as a Service as an economical and flexible solution for their security needs. By leveraging the specialized knowledge and resources provided by managed service providers, organizations are able to maintain a robust defense against cyberattacks while focusing on their core competencies.
Components of SOC as a Service
The components of SOC as a Service play an essential role in today’s cybersecurity landscape. With the increasing number and sophistication of cyberattacks, organizations are embracing managed SOC services to protect their sensitive data and maintain operations. By partnering with a trusted SOC as a Service provider, businesses are able to ensure their cybersecurity risk management strategy is effective and compliant with industry standards.
One critical aspect of SOC as a Service is threat hunting and response. In this proactive approach, security analysts continually search for potential vulnerabilities within the network of an organization by monitoring any unusual patterns or behaviors that indicate malicious activity. By identifying all of these hidden threats early on, companies are able to prevent breaches from occurring or mitigate their impact if they do happen. Threat-hunting teams use various tools, techniques, and intelligence sources in order to uncover lurking dangers before they can cause real and lasting damage.
Managed SOC services also include comprehensive cybersecurity risk management strategies that enable organizations to stay ahead of emerging threats. By providing continuous monitoring, assessment, and reporting capabilities, these services help businesses identify vulnerabilities in their systems and quickly develop robust protocols to address them. With the right partner, companies are able to enhance their overall cyber resilience by implementing risk management measures tailored to their unique needs.
Cybersecurity compliance is another component of SOC as a Service solutions. Organizations have to ensure they remain compliant with regulations like GDPR (General Data Protection Regulation) in Europe and HIPAA (Health Insurance Portability and Accountability Act) in the United States. A competent SOC as a Service provider aids in maintaining adherence to these regulations by providing automated compliance checks, regular audits, detailed reporting mechanisms, and expert guidance on navigating relevant legislation.
Cyber incident response plays an integral part in SOC as a Service offerings. When faced with a security breach or attack, organizations must have well-defined processes in place that facilitate rapid detection, containment, eradication of threats, and swift recovery of systems and data. SOC as a Service providers can assist with these efforts by supplying specialized expertise, incident response playbooks, and access to advanced security tools that minimize the impact of cyber incidents on business operations.
Pondurance is an example of a managed service provider that offers both incident response and managed detection and response services for companies of all sizes. Its team of incident responders, incident handlers, and forensics and malware specialists can coordinate a full incident response from the moment a threat is identified. This is a critical area for protecting the company not only from the costs of a ransom but also from operational disruption, destruction, loss of intellectual property, and damage to customer relationships and brand reputation.
Ultimately, partnering with a trusted SOC as a Service provider offers numerous benefits for businesses of the modern day digital landscape. By providing proactive threat hunting and response capabilities, comprehensive cybersecurity risk management strategies, assistance with regulatory compliance, and expert support during cyber incident responses, these managed SOC services help organizations stay ahead of evolving threats while maintaining security postures. As the complexity of cybersecurity challenges continues to grow, having a reliable partner will become increasingly essential for companies wanting to safeguard their valuable assets and maintain operational continuity.
SOC as a Service Benefits
SOC as a Service is an innovative approach to security monitoring and management that has become increasingly popular due to its numerous benefits for organizations of all sizes. By outsourcing their security operations center functions to experts, businesses can leverage advanced capabilities and expertise without the need to build and maintain a full-scale on-site SOC.
One significant benefit of SOC as a Service is the integration of endpoint detection and response (EDR) solutions. EDR technology provides continuous monitoring and analysis of endpoint activities, enabling swift detection of potential threats at their point of entry into a network. By leveraging EDR within a managed SOC environment, organizations can benefit from real-time threat intelligence and rapid response capabilities that minimize damage in the event of cyber attacks.
In addition to EDR, another essential component of SOC as a Service is network detection and response (NDR). NDR solutions focus on identifying unusual or malicious activities within an organization’s network infrastructure by analyzing traffic patterns and other network-related data. Combining NDR with EDR capabilities within a managed SOC service ensures visibility into potential security incidents, allowing for faster detection and more accurate remediation.
Organizations that opt for SOC as a Service often engage services from an MDR consultant or Managed Detection and Response provider. These consultants carry out various tasks such as threat hunting, incident response planning, and vulnerability management. MDR consultants help businesses enhance their threat identification capabilities while ensuring that they are equipped with the right tools for dealing with any potential breaches.
Pondurance is an MDR consultant that safeguards against cyberattacks. Its internal IT/cybersecurity detects threats with the latest technologies and provides cybersecurity assistance 24/7. While outsourcing your sensitive data to a consultant might initially raise concerns, Pondurance ensures its customers retain full control over their information.
The role of SOC analysts within these managed services is crucial for constant monitoring, analysis, and correlation of security events across all layers of an organization’s IT environment. They work closely with MDR consultants to promptly investigate and resolve any detected anomalies before they escalate into critical incidents.
In conclusion, the benefits offered by adopting SOC as a Service are numerous. By leveraging the expertise and capabilities of third-party providers, organizations are able to protect their digital assets more effectively than ever before. Enhanced endpoint detection and response, network detection and response, and the support of MDR consultants and SOC analysts allow for seamless integration of advanced security tools with minimal internal resource allocation. This comprehensive approach to cybersecurity helps organizations stay one step ahead in an ever-evolving threat landscape while focusing on core business objectives.