Our privacy policy is located here.
Risk-Based Cybersecurity
with Managed Detection and Response and Pondurance Security Operations Center (SOC) Services
What is a Security Operations Center?
A SOC is the right collection of technologies and people–security analysts, threat hunters, threat intelligence and incident response experts—all working together to detect and respond to cyberthreats and reduce your risk.
"A SOC is a centralized function operating as first responders for attempted intrusions with responsibilities that include detection, analysis, investigation and response on a 24/7 basis.”
– Forrester Opportunity Snapshot: July 2022
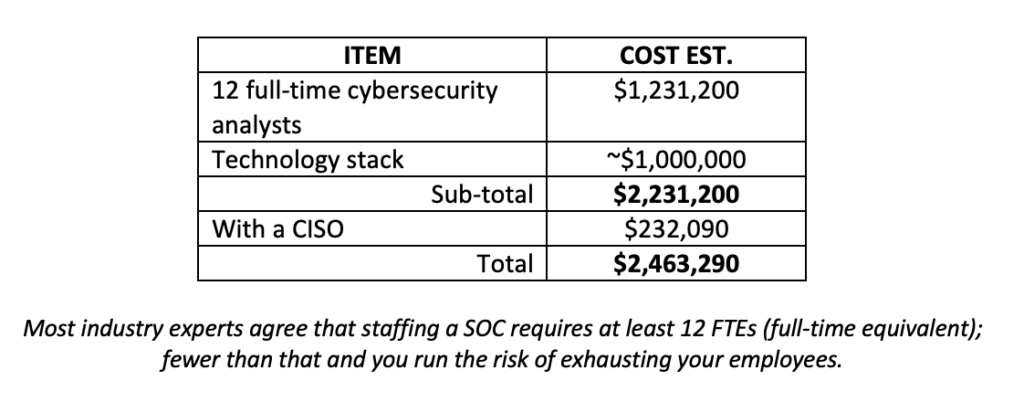
Building your Own SOC Vs. Outsourcing
Pondurance MDR and SOC Services
Gartner Says:
Pondurance Agrees:
See how Pondurance Aligns with what Gartner Recommends for MDR
Ready to Start the Conversation with a Pondurance Expert?
Get a risk assessment or request a demo today to get started!
Security Operations Center
A security operations center (SOC) serves as the nerve center for an organization’s cybersecurity defense, tasked with monitoring, detecting, analyzing, and responding to cyber threats. These dedicated teams of IT security professionals, often associated with top cybersecurity companies, leverage cutting-edge technology and processes to protect digital assets from cyber risks such as unauthorized access, data breaches, and malicious activities. The SOC’s primary goal is to provide informed security, ensuring that potential threats are identified early and addressed swiftly to mitigate potential impacts and maintain the integrity of information systems.
One of the fundamental functions of a SOC is real-time monitoring and threat detection. Using a suite of tools including intrusion detection systems, firewall logs, and vulnerability scanners, SOC analysts continuously monitor network traffic and system activities, proactively identifying any signs of cyber threats or suspicious behavior. This proactive approach allows organizations to stay ahead of cyber threats, preventing potential data breaches and other security incidents.
Furthermore, the SOC plays a crucial role in coordinating incident response efforts. In the event of a security breach, the SOC team conducts thorough forensic analysis, implements containment measures, and initiates remediation steps to minimize the impact of the cyber threat. Collaborating with various departments such as legal, public relations, and human resources, the SOC ensures that all aspects of incident management are addressed promptly and effectively.
In recent years, there has been a growing trend towards adopting security operations centers as a service model, particularly among small- to medium-sized businesses. Outsourcing cybersecurity operations to specialized firms like Pondurance, which offers Managed Detection and Response (MDR) services, provides organizations with access to advanced protection against cyber threats without the significant upfront investment or ongoing maintenance costs associated with building an in-house SOC.
Beyond the technical aspects, the definition of a security operations center also encompasses organizational culture around cyber risk management. By promoting cybersecurity best practices and fostering a culture of security awareness among employees, organizations can significantly enhance their security posture and reduce the likelihood of successful cyber attacks.
In conclusion, a security operations center is a cornerstone of any comprehensive cybersecurity strategy. Whether through internal resources or external partnerships with cybersecurity firms, implementing a SOC enables organizations to effectively monitor for potential threats, respond rapidly to security incidents, and strengthen their overall cybersecurity posture, safeguarding sensitive data and ensuring business continuity in an increasingly digital world.
Security Operations Center as a Service
In today’s rapidly evolving cyber threat landscape, a security operations center as a service (SOCaaS) has emerged as a vital component of any robust cybersecurity strategy. This innovative approach to cybersecurity combines the functionality of a traditional security operations center with the convenience and scalability of cloud-based services. By leveraging SOCaaS, organizations can effectively protect their digital assets and sensitive data from ever-increasing cyber-attacks.
One crucial aspect to consider while evaluating SOC-as-a-service providers is their ability to offer managed detection and response (MDR) capabilities. MDR refers to the continuous monitoring, analysis, investigation, and response to cyber threats in real time. It is an essential element in modern cybersecurity strategies as it enhances the efficiency and effectiveness of the overall security posture. Hence, when searching for a reliable SOCaaS provider, it is crucial to ensure that MDR capabilities are included in their offerings.
But what does MDR mean in SOC?
In simple terms, MDR is an advanced service that goes beyond traditional security measures such as antivirus software or firewalls. It provides comprehensive protection by constantly examining the organization’s systems for signs of malicious activity and responding proactively to potential threats before they cause damage. As such, having MDR integrated into your SOCaaS solution ensures that your organization benefits from cutting-edge security technologies designed to counter sophisticated cyber-attacks.
Is an MDR a SOC?
One might ponder: Is Managed Detection and Response (MDR) the same as a Security Operations Center (SOC)? Although these terms are sometimes used interchangeably, they actually denote distinct elements within the larger cybersecurity landscape. A SOC serves as the nerve center, overseeing the monitoring and administration of diverse security solutions deployed throughout an organization’s IT infrastructure. On the other hand, MDR encompasses specialized services dedicated to identifying and thwarting advanced threats that might evade traditional security measures.
Do you need SOC as a Service?
So why do you need a SOC as a service? The primary reason lies in its ability to provide round-the-clock protection against increasingly complex cyber threats. With limited in-house resources and a growing number of online risks, organizations can no longer rely solely on traditional security mechanisms to safeguard their digital assets. A SOCaaS solution offers continuous monitoring, advanced threat detection, timely response, and expert guidance from seasoned cybersecurity professionals. By leveraging these benefits, businesses can effectively reduce the risk of data breaches and maintain a high level of security within their IT environment.
Security operations center as a service (SOCaaS) is an indispensable tool for modern-day cyber defense strategies. By integrating managed detection and response (MDR) capabilities into your SOCaaS solution, you can significantly strengthen your organization’s security posture and protect it from sophisticated cyber-attacks. When evaluating potential providers, make sure to consider the importance of MDR services and select a provider capable of offering comprehensive protection to meet your unique cybersecurity requirements.
Components of Modern Security Operations Centers
The components of modern Security Operations Centers (SOCs) have emerged as indispensable tools for organizations aiming to safeguard their digital infrastructure against evolving cyber threats. These centers are meticulously designed to enable continuous monitoring, detection, and response to potential security incidents within an organization’s network, ensuring seamless operations with minimal disruption. The frameworks and components deployed in these SOCs are pivotal in fostering a secure environment for mission-critical data and operations.
Central to an effective SOC is the role of the security operations center analyst. These adept professionals are entrusted with the critical task of monitoring networks for suspicious activities, identifying potential threats, and analyzing cybersecurity incident trends. Serving as the frontline defense against cyber-attacks, they swiftly detect intrusions and implement appropriate containment measures to mitigate damage. Their proficiency in threat intelligence equips them to anticipate emerging attack vectors and tactics employed by cybercriminals, rendering them invaluable assets in maintaining a resilient security posture.
A cornerstone of any successful SOC lies in its Cyber Security Operations Center framework. This framework encompasses a set of policies, procedures, and guidelines delineating how various teams within an organization should collaborate while responding to security incidents. It also delineates the tools and technologies employed for each phase of incident detection, analysis, containment, eradication, recovery, and post-mortem reviews.
By embracing a well-defined framework that fosters inter-team communication and expeditious execution of tasks during incidents, organizations can significantly abbreviate the time required to detect threats and mount effective responses. Threat intelligence assumes a pivotal role in augmenting the capabilities of a modern SOC. It encompasses insights garnered from various sources such as internal data analytics systems or external threat intelligence feeds, aiding in the identification of potential vulnerabilities within an organization’s network or systems and providing insights into potential attacker strategies. By embedding threat intelligence into their daily operations, SOCs can proactively monitor potential threats and implement countermeasures before adversaries can inflict damage.
The effectiveness of a SOC hinges on its adept fusion of advanced technology with human expertise. While artificial intelligence and automation streamline processes and reduce response times, it is imperative not to overlook the significance of human intuition and experience in combating intricate cyber threats. As adversaries are not mere machines but individuals, harnessing this human element furnishes a crucial advantage in fortifying an organization’s digital assets.
Incorporating these pivotal components within a Security Operations Center empowers organizations to detect and respond adeptly to cyber threats, thereby diminishing their risk exposure. By investing in these elements, businesses across diverse sectors can fortify their cybersecurity posture, ensuring operational resilience in an ever-expanding digital landscape.
Best Practices for a Robust Security Operations Center
The evolution of robust Security Operations Centers (SOCs) over the years underscores organizations’ increasing recognition of the imperative to safeguard their valuable assets from cyber threats, including potential data breaches and cyber risk. Beyond traditional cybersecurity solutions, a robust SOC integrates advanced tools and techniques to bolster threat hunting and response capabilities, enhancing informed security and cyber threat assessment. This section will explore key best practices for establishing and maintaining an effective SOC.
SOC as a service has gained popularity among businesses for its comprehensive cybersecurity support without substantial upfront investments, offering tailored cyber risk management and threat intelligence services. Partnering with experienced SOC providers grants access to cutting-edge tools incorporating AI, machine learning, and big data analytics, enhancing threat detection and incident response capabilities while improving security posture and vulnerability management.
Effective cyber incident response management is a cornerstone of a robust SOC, necessitating well-defined processes for identifying, analyzing, containing, eradicating, and recovering from security breaches, mitigating potential impacts on information systems and sensitive data. Communication and collaboration among different teams within the organization are crucial for streamlining incident response and maintaining a proactive stance against cybersecurity threats.
Skilled cybersecurity analysts who engage in proactive threat hunting are vital for an effective SOC, actively searching through networks and systems to detect potential threats before they manifest, contributing to informed security decisions and proactive risk assessments.
Continuous improvement is key for SOCs, involving regular performance evaluations, post-incident reviews, and refinement of internal processes to adapt to the ever-changing threat landscape and strengthen the risk management strategy. Training programs for all staff members ensure they remain updated with industry developments and emerging threats, contributing to a highly skilled workforce essential for maintaining SOC effectiveness and resilience against potential threats.
Collaboration with external organizations and industry partners, through sharing threat intelligence and engaging in joint incident response efforts, enhances overall threat hunting and response capabilities, fostering a proactive approach to cybersecurity and informed decision-making.
In summary, establishing and maintaining an effective SOC requires a combination of advanced tools, skilled personnel, well-defined processes, and continuous improvement initiatives. Incorporating these best practices significantly enhances an organization’s cyber defense posture, ensuring real-time detection and response to cyber threats while maintaining mission-critical operations without disruption. Whether through internal development or outsourcing to SOC service providers like Pondurance, a top cybersecurity company, a strong SOC is essential for safeguarding digital assets and maintaining business continuity in today’s threat landscape.
Related Topics
- Cybersecurity Compliance Framework
- Cybersecurity For Small Business
- Soc As A Service
- Cybersecurity Compliance
- What Is Penetration Testing
- Nist Cybersecurity
- Cybersecurity Penetration Testing
- Vulnerability Scan
- Cybersecurity Resources
- Cybersecurity Risk Assessment
- Nist Compliance
- Cybersecurity Risk Management
- Cybersecurity Assessment Tool
- Cybersecurity Healthcare
- Cybersecurity Consulting Firms
- Cybersecurity Assessment
- Risk Based Cybersecurity
- How To Prevent Malware Attacks
- Pci Dss
- Cybersecurity Consultant
- Nist Csf
- Penetration Testing Companies