

We thought we had been making the right security investments. Then we had an incident and brought in Pondurance. They immediately proved their value and earned our trust due to their immense expertise and guidance throughout the entire process. We simply wouldn‘t have been successful without them.
Steve Long, President & CEO, Hancock Health
Want to review more case studies? LEARN MORE
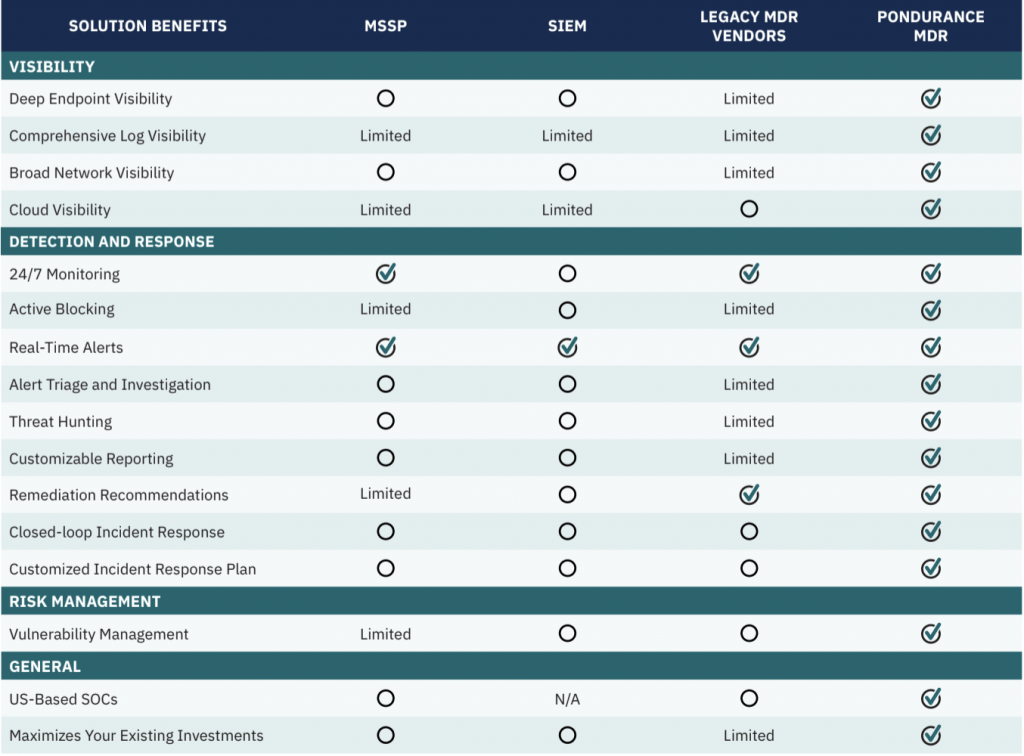
Download our comparison chart to see the difference between SIEMs, MSSPs, other MDRs and Pondurance MDR.



Endpoint detection and response (EDR) is a pivotal technology for cybersecurity companies, addressing the pressing need to continuously monitor and safeguard network-connected devices. These endpoints, spanning from laptops to IoT gadgets, are vulnerable to cyber risk without proper management. By integrating advanced threat intelligence, behavior analysis, and real-time monitoring capabilities, EDR efficiently identifies and mitigates potential security risks associated with endpoint devices.
Understanding the significance of endpoint detection and response sheds light on its crucial role in cyber risk management. As cyber threats become increasingly sophisticated, traditional antivirus solutions fall short in protecting businesses from potential data breaches and cyber risk. EDR takes a proactive stance, leveraging data from endpoints to detect and thwart security threats before they can wreak havoc on information systems.
In the landscape of cybersecurity defense strategies, Pondurance stands out among the top cybersecurity companies, offering comprehensive endpoint detection and response services. Pondurance’s approach prioritizes risk assessment and informed security decisions, delivering tailored EDR solutions that align with clients’ unique needs and security teams’ capabilities.
As organizations navigate the complex realm of cybersecurity technologies, distinguishing between EDR, XDR, MDR, and SIEM becomes imperative. While EDR focuses primarily on endpoint protection, eXtended Detection and Response (XDR) broaden the scope by integrating multiple security layers. Managed Detection and Response (MDR) provides round-the-clock monitoring by external security experts, while Security Information and Event Management (SIEM) aggregates log data for analysis and correlation.
Amid the array of cybersecurity options, opting for a managed endpoint detection and response service like Pondurance streamlines the process of cyber risk reduction. Pondurance’s EDR services combine cutting-edge technology with expertise in threat intelligence and risk management, fortifying organizations’ security posture against potential threats and sensitive data breaches.
In conclusion, endpoint detection and response emerge as indispensable elements of a robust cybersecurity strategy. Businesses must assess their security landscape and leverage advanced EDR services like Pondurance to effectively combat evolving cyber threats and enhance their overall security posture.
Endpoint detection and response (EDR) emerges as a critical facet of modern cybersecurity, emphasizing the monitoring, detection, and analysis of threats at the endpoint level. These cybersecurity companies’ tools enable organizations to fortify their defenses against potential cyberattacks, thereby safeguarding sensitive data from cyber risk.
A notable advantage of endpoint detection and response lies in its provision of real-time monitoring and analysis capabilities for potential security threats. This proactive approach empowers companies to preemptively identify vulnerabilities, mitigating the risk of data breaches and other cybercrimes. Additionally, EDR solutions facilitate the early detection of targeted attacks, affording organizations an opportunity to respond promptly and minimize any potential impacts.
In today’s market, an array of EDR tools caters to diverse organizational needs, boasting features such as behavioral analysis, integration with threat intelligence, automated incident response, and advanced analytics. Leading examples include Carbon Black Response, CrowdStrike Falcon Endpoint Protection, Microsoft Defender for Endpoint, and Cisco AMP for Endpoints.
A common query in evaluating EDR solutions pertains to their comparison with Security Information and Event Management (SIEM) systems. While both technologies are integral to cybersecurity strategies, they serve distinct functions. SIEM focuses on correlating events across multiple devices to detect patterns indicative of security incidents, whereas EDR specializes in endpoint threat detection through continuous endpoint activity monitoring.
Organizations seeking comprehensive protection often opt to implement both SIEM and EDR solutions, leveraging the strengths of each technology to address potential security gaps effectively.
Pondurance stands as an exemplar in delivering exceptional endpoint detection and response services. Their customized approach enables clients to prioritize risks specific to their environments, tailoring protection measures accordingly. By adopting a proactive stance against potential cyber threats and focusing on each client’s unique requirements, Pondurance ensures the highest level of security.
In summary, endpoint detection and response assume paramount importance in contemporary cybersecurity strategies. Through the integration of EDR tools and SIEM systems, organizations can establish comprehensive protection for their infrastructure, mitigating the evolving landscape of cyber threats. As cybercriminals grow increasingly sophisticated, investing in robust EDR solutions like those offered by Pondurance becomes imperative for maintaining proactive security measures.
Endpoint detection and response (EDR) solutions have emerged as crucial elements in the dynamic landscape of cybersecurity. As organizations face increasingly sophisticated threats like ransomware, data breaches, and targeted attacks, the demand for robust endpoint protection intensifies. Leading cybersecurity companies, including CrowdStrike EDR, offer advanced tools and services to detect, analyze, respond to, and remediate security incidents effectively.
In selecting an endpoint detection and response service, businesses must consider various factors, including efficacy and pricing. EDR pricing structures vary based on features, organization size, and additional services required, with some vendors offering tiered options to accommodate different budgets.
Distinguishing between endpoint protection and endpoint detection and response is essential. While endpoint protection focuses on preventing malware attacks through traditional means, EDR takes a proactive approach, continuously analyzing endpoints for suspicious activities that may bypass standard protections.
Pondurance’s EDR services are tailored to individual business needs, leveraging risk assessment to provide efficient yet comprehensive protection without compromising security resources.
A comprehensive EDR solution should encompass features such as advanced threat hunting, automated incident response workflows, behavior-based analytics, and integrated intelligence feeds. Additionally, expert implementation support is vital in minimizing risks associated with configuration errors.
Top EDR tools serve diverse industries, offering innovative product offerings and responsive technical support to address emerging cyber threats effectively.
In summary, endpoint detection and response are critical components of cybersecurity strategies. By investing in reputable EDR solutions like those from CrowdStrike or Pondurance, organizations can bolster their defenses against advanced threats while maintaining control over their technology infrastructure. Staying ahead of evolving cybercrime requires leveraging tailored EDR solutions that align with specific needs and budget constraints.
Endpoint detection and response (EDR) examples are paramount in grasping the significance of these cybersecurity solutions. EDR, which stands for Endpoint Detection and Response, offers organizations robust protection against modern-day threats by monitoring and analyzing system endpoints. This proactive approach enables EDR solutions to detect potential security breaches, respond effectively, and adapt to evolving cyber-attack methods.
In today’s digital environment, the importance of robust endpoint detection and response examples cannot be overstated. With the proliferation of connected devices on corporate networks, the risk of security breaches escalates as hackers devise increasingly sophisticated attack strategies. Effective EDR solutions provide real-time visibility into potential security threats across all endpoints, empowering businesses to outmaneuver attackers.
Pondurance’s endpoint detection and response services encompass a wide range of features to safeguard systems against malicious activity. Setting Pondurance apart is its focus on delivering tailored protection based on individual risk profiles and user priorities.
Rather than adopting a one-size-fits-all approach, Pondurance customizes its EDR solutions to meet specific user needs, considering industry requirements, compliance regulations, and unique business challenges. This comprehensive approach ensures thorough protection of an organization’s digital assets.
Moreover, Pondurance combines state-of-the-art technology with human expertise to provide unparalleled protection through its endpoint detection and response examples. By integrating advanced machine learning algorithms with dedicated cybersecurity teams that monitor network activities around the clock, Pondurance swiftly identifies any suspicious behavior or potential threats.
In conclusion, implementing robust Endpoint Detection and Response services, such as those offered by Pondurance, is imperative in today’s rapidly evolving digital landscape. By proactively addressing the latest threats and adapting to each organization’s unique requirements, these customized EDR solutions offer invaluable protection against cyber-attacks, enabling businesses to thrive securely and confidently.
Endpoint detection and response (EDR) tools have become crucial components in the cybersecurity landscape as organizations seek to protect their digital assets against the ever-evolving threat landscape. These tools offer comprehensive and real-time monitoring and analysis of endpoint activities, allowing for rapid identification and mitigation of potential security threats. In this article, we will explore some of the best EDR tools available in the market, understand their importance in enhancing security posture, and take a closer look at Pondurance’s EDR offerings.
EDR security is designed to provide advanced protection for endpoints, which are often targeted by cybercriminals looking to gain unauthorized access or execute malicious actions within an organization’s network. The full form of EDR stands for Endpoint Detection and Response – a clear indication that these tools focus on detecting unusual or malicious behavior on endpoints like laptops or servers, while simultaneously providing swift response measures to minimize damage.
Top 10 EDR tools include prominent names such as Carbon Black, CrowdStrike Falcon, Cybereason, FireEye Endpoint Security, Microsoft Defender ATP, Palo Alto Networks Cortex XDR, SentinelOne, Sophos Intercept X Advanced with EDR, Symantec Endpoint Security Complete (Broadcom), and VMware Carbon Black Cloud. These products offer various features such as behavioral analysis, threat intelligence integration, incident investigation capabilities, and automated remediation actions.
Pondurance’s endpoint detection and response services are unique in that they provide tailored protection based on an organization’s risk profile and specific needs. By understanding what is important to a business from a security standpoint, Pondurance can implement tailored strategies that focus on safeguarding critical assets while minimizing impact on overall operations.
Examples of how Pondurance’s EDR services work include utilizing industry-leading threat intelligence feeds to identify emerging threats proactively; leveraging machine learning algorithms to detect anomalous behavior indicative of a potential breach; conducting thorough investigations into incidents to determine root causes; and delivering actionable insights aimed at bolstering security measures and preventing future incidents.
In conclusion, endpoint detection and response tools are essential components of an organization’s overall cybersecurity strategy. As the threat landscape continues to evolve, investing in robust EDR tools ensures businesses can proactively detect, analyze, and respond to potential security incidents. Pondurance’s EDR services offer comprehensive protection that factors in an organization’s unique risk profile and requirements, helping them maintain a strong security posture while focusing on their core business objectives.