Our privacy policy is located here.
Cyberattacks continue to occur at an alarming pace, which probably comes as no surprise to most manufacturers. In 2022, the manufacturing industry experienced 1,817 incidents and 262 breaches with confirmed data disclosures, according to Verizon’s 2023 Data Breach Investigations Report. The report also found that hacking, malware, and social engineering attacks are the most prevalent attack patterns on manufacturers.
The manufacturing industry is a prime target for cyberattackers, particularly those using ransomware, since manufacturers often pay the ransom when attacked. That’s because even a small amount of downtime for a manufacturer can make an impact, causing production line stoppage and supply chain disruptions. In addition, many manufacturers use legacy systems that can’t be properly patched or updated, leaving them vulnerable to an attack.
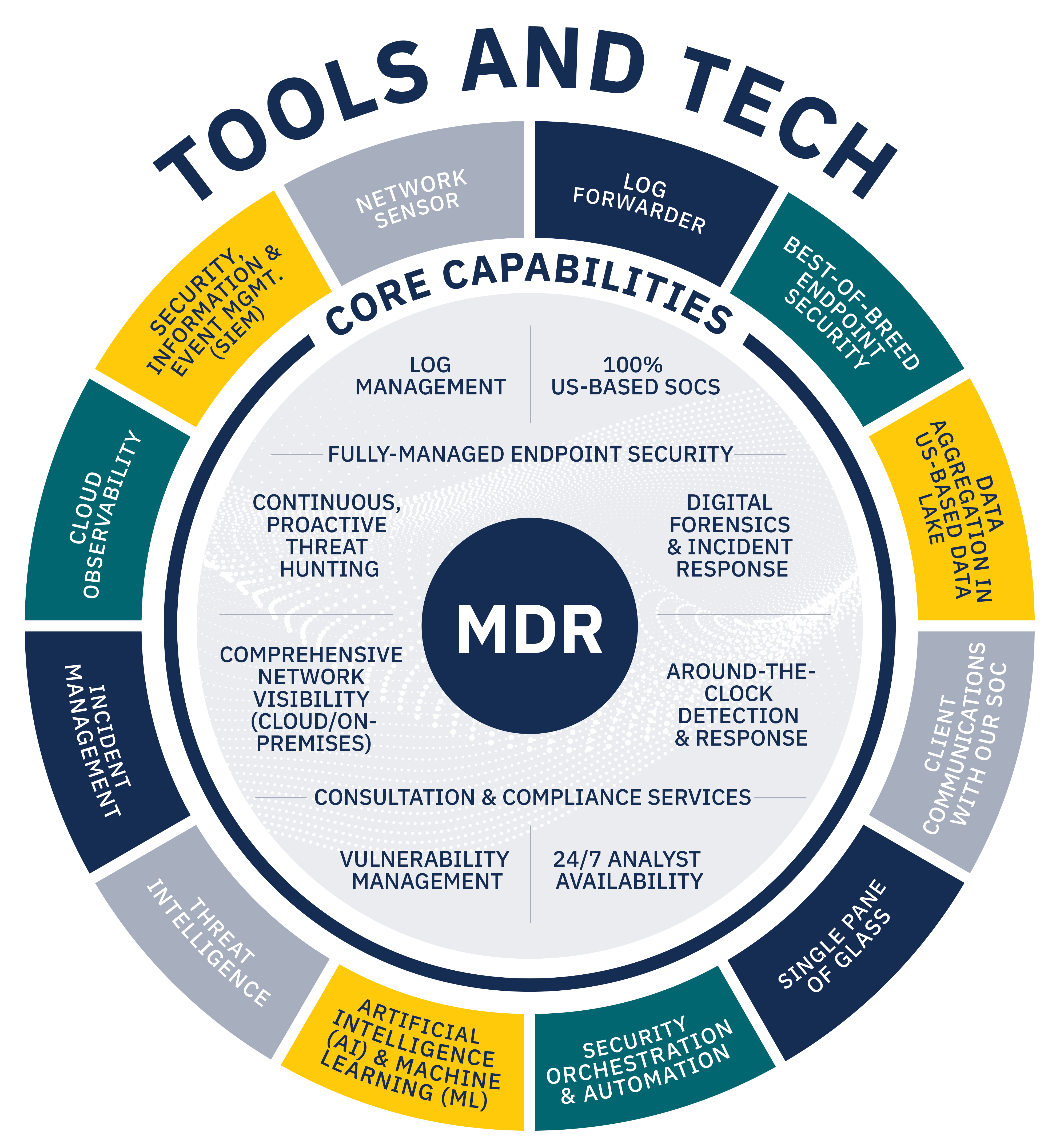
To combat these risks, many manufacturers are turning to managed detection and response (MDR) services, a category of security solutions that offers the technology, process, and humans needed to defend against the increasing threat of cyberattacks. Technological research and consulting firm Gartner projects that 50% of all organizations will use MDR services by 2025.
But not all MDR providers are created equal. Manufacturers looking for an MDR provider in the evolving cyber landscape are having to sort through the confusion to find the right MDR provider for their needs. Pondurance keeps it simple. We offer modern MDR, cybersecurity consulting, and 24/7 incident response and threat hunting to help manufacturers like you stay safe from cyberattacks and disruption.
After reading this guide, you will have a better understanding of available MDR services and how those options may align with your needs. The guide covers:
- Exploring MDR’s history
- Simplifying the need for complex technology
- Fighting cyberattackers with human defenders
- Bringing the ‘R’ to MDR
- Customizing solutions for today and tomorrow
- Understanding your industry
- Tailoring to your needs and budget
† 2021 Gartner Market Guide for Managed Detection and Response Services, Gartner, October 2021.