Our privacy policy is located here.
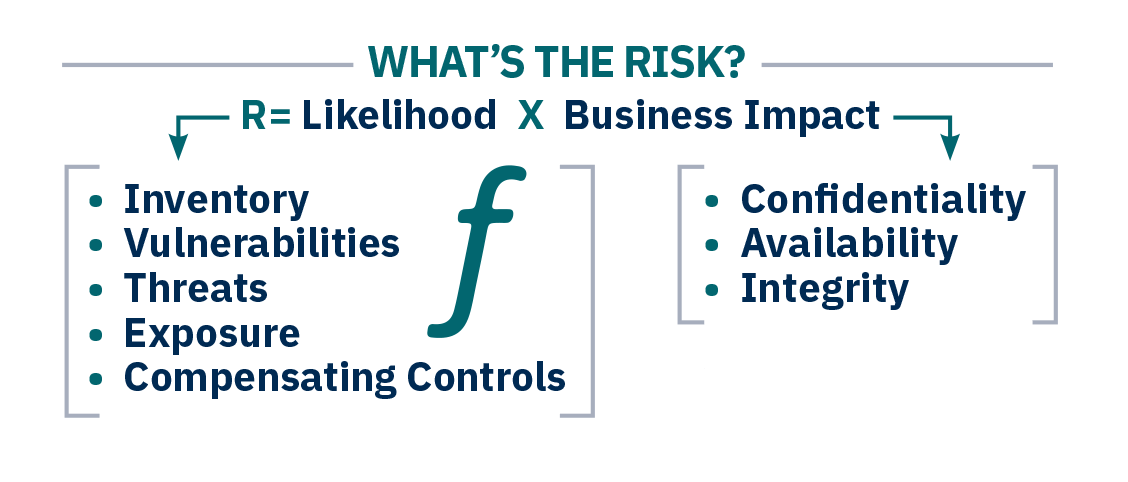
Your company has its own unique set of cyber risks. Your lines of business, your technical infrastructure, threats, employees, third-party vendors, and other variables all factor into your cyber risk profile. Each year, risks continue to grow more complex and new threats raise their ugly heads. Though you can’t control the evolving cyber landscape, you can control your cybersecurity strategy. But what’s the best strategic approach to cybersecurity today?
Many companies take a generic approach to cybersecurity where they adopt a standardized program and simply check the boxes as they reach predetermined security milestones. Other companies use a “random acts of security” approach where they reactively put new technologies in place without having a strong strategy behind their actions. However, neither of these approaches considers what the company truly needs in a cybersecurity program. But risk-based cybersecurity does.
This ebook helps define a risk-based approach to cybersecurity and outlines the steps you need to consider.



