


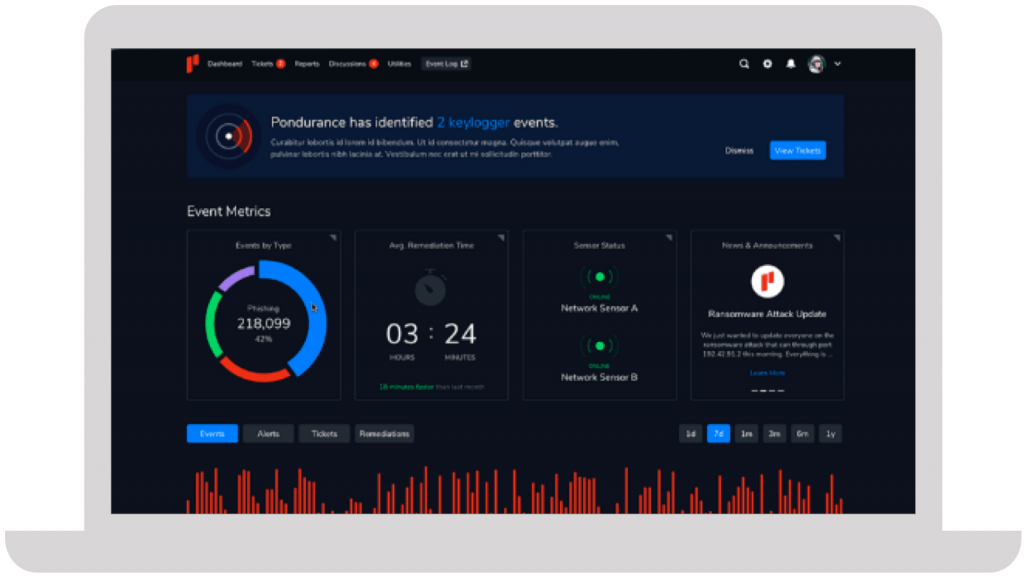
We take a personalized approach to developing your cybersecurity program. Instead of an all-or-nothing approach like other MDR providers, Pondurance lets you pay for what you need, without sacrificing the visibility and transparency you want.


The number of data breaches continues to escalate, putting small businesses on high alert. Nowadays, any information that a business finds valuable is monetizable and a potential target for attack. Learn more in our eBook.
Your company has its own unique set of cyber risks. Though you can’t control the evolving cyber landscape, you can control your cybersecurity strategy. But what’s the best strategic approach to cybersecurity today? Learn more in our eBook.
Join us on-demand to discuss components of MDR and how to choose the right provider for your organization.
They immediately proved their value and earned our trust due to their immense expertise and guidance throughout the entire process.
Steve Long, CEO @ Hancock Health