Data Breach Notifications With haveibeenpwned.com
Pondurance September 24, 2021
Data breaches are frequently occurring, and the scale to which they affect organizations and users is massive. Oftentimes, organizations receive data breach notifications via third parties after the incident. As an organization, how are you supposed to react to this type of communication? For those that need more knowledge into which of your accounts have been affected, we recommend using Have I Been Pwned (HIBP). It is a free online tool that can help organizations and individuals learn if their accounts are compromised. It aggregates the data of compromised accounts to help users and organizations better protect themselves from the risks of cyberattacks.
Conducting Domain Searches
To get started, go to the HIBP website here and verify that the domain belongs to your organization.
Data Breach Notification Actions and Considerations
- Understand the extent of the breach by searching for the compromised website here.
- This will include a list of data such as breach date and compromised data.
- It is important to note whether usernames and passwords appear in the compromised data section of the breach.
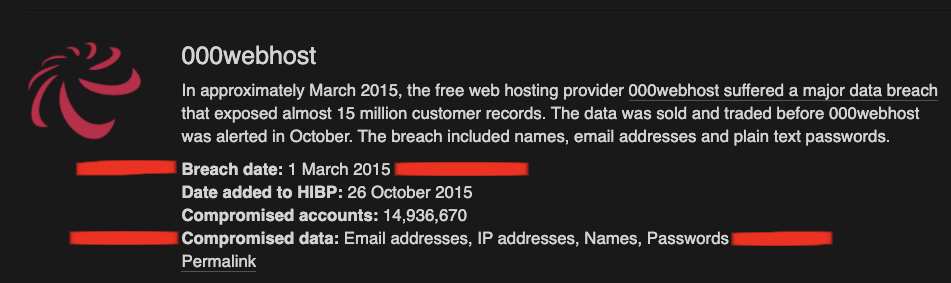
- View the data provided by HIBP to find the accounts that are compromised and understand the impact of the breach within the environment. This will also give a scope of compromised users to address in future steps.
- If the compromised data includes passwords and usernames, we recommend that you review the last password change date for that user account to ensure that the account has had a password change or rotation since the date of the breach.
- If there is uncertainty regarding the password change, we recommend that the password immediately be reset to ensure that the account cannot be accessed via stored credentials on the compromised website.
- We recommend that staff caution users who utilize work emails when registering for websites for personal use to help avoid the likelihood of appearing in this style of breach.
- We also recommend that staff educate users not to utilize the same password for personal use as they do for business use.
- For all data breach notifications that contain a more recent breach and critical information such as a password that was leaked, be sure to review the user’s login activity in your user management consoles.
- For users who perform critical functions or are considered VIP users, we recommend that they sign up here to be notified if their accounts are found in a future breach.
When in doubt, Microsoft has great recommendations regarding password policies and management to follow, including:
- Maintain an 8-character minimum length requirement.
- Don’t require character composition requirements (e.g., *&^%$).
- Don’t require mandatory periodic password resets for user accounts.
- Ban common passwords to keep the most vulnerable passwords out of your system.
- Educate your users to not reuse their organization passwords for non-work-related purposes.
- Enforce registration for multifactor authentication.
- Enable risk-based multifactor authentication challenges.
Are you interested in learning more about protecting your personal information and curating a safer experience online? Download our Employee Security Awareness Checklist for the best practices for online security.
