Vulnerability Management Is Critical To Preventing Cyberattacks — What You Need To Know
Pondurance August 26, 2021
It only takes one unpatched vulnerability to result in a costly data breach, ransomware or malware attack. The National Institute of Standards and Technology (NIST) logged more than 18,000 vulnerabilities in 2020, and more than half were critical or of high severity. 1 This is the highest number of vulnerabilities NIST has seen to date.
Software vulnerabilities are one of the main sources of cyberattacks, such as REvil ransomware’s supply chain attack against Kaseya Ltd. and the Accellion vulnerability that affected healthcare data. Organizations are under a lot of pressure to stay secure and compliant while cyberattacks are increasing. When managing vulnerabilities and the alerts that come with them, how do you know which ones pose the biggest risk? And which should you prioritize first?
What is a vulnerability?
A vulnerability is a weakness that can be exploited by a threat actor. The actor uses any means possible to gain unauthorized access or privileged control to an application, network, service, endpoint, or server. Examples include exploiting communication ports open to the internet and unsecure configurations of either outdated software or operating systems (OS). Attackers scour systems to find these vulnerabilities, gain access, and infect systems with malware or encryption that leads to severe ransomware attacks.
Vulnerabilities that are abused by attackers often result in:
- Theft of sensitive data.
- Harm to systems and applications.
- Ransomware and/or malware infection (along with ransom demands).
- Regulatory violations.
- Damage to an organization’s reputation and negative media exposure.
It’s critical to patch vulnerabilities to reduce risk but with a large number of daily alerts, it’s hard to understand which to prioritize first.
How are vulnerabilities defined?
The National Vulnerability Database (NVD), maintained by the NIST, is the most popular repository of vulnerability information. This is an open, standards-based effort using the security content automation protocol (SCAP) standard, which has a few components:
Common vulnerabilities and exposures (CVE) – Each CVE enumerates and defines a specific vulnerability that could be subject to an attack for public knowledge.
Common configuration enumeration (CCE) – A CCE is a list of system security configuration issues used to improve workflow by facilitating fast and accurate connecting configuration data across multiple information sources and tools.
Common platform enumeration (CPE) – CPE is a standardized method of describing and identifying classes of applications, operating systems, and hardware devices present among an enterprise’s computing assets. They are used to describe what a CVE or CCE applies to.
Common vulnerability scoring system (CVSS) – CVSS is an open standard scoring system to assign scores to a vulnerability that indicates its severity. It offers visibility into prioritizing remediation efforts and resources according to the threat. Scores range from 0 to 10, with 10 being the most severe.
Many public sources of vulnerability definitions exist and are freely available, such as Microsoft’s security updates. Additionally, several vendors offer access to private vulnerability databases via paid subscription.
What is vulnerability management?
Vulnerability management is the process of identifying, categorizing, prioritizing, and resolving vulnerabilities in digital assets such as applications, servers, endpoints, cloud infrastructure, servers, etc. Vulnerability management is one of the most proactive methods to identify weaknesses within your digital assets. These weaknesses can pose a threat to your digital ecosystem and, if addressed early, can reduce risks to your digital ecosystem.
Every year, new vulnerabilities are discovered and require skilled security analysts to prioritize, patch, or reconfigure these weaknesses and proactively address vulnerabilities before they are utilized for a cyberattack. Organizations serious about the security of their environment should implement vulnerability management into their cybersecurity strategies to provide the highest levels of security posture possible.
While mitigating threats is a reactive process where the threat must be actively present, vulnerability management is proactive, identifying and prioritizing potential threats to close the security gaps that exist before attackers take advantage of them.
What is the vulnerability management process?
Every new vulnerability introduces risk to the organization. So, a defined process is often used to provide organizations with a way to identify and address vulnerabilities quickly and continually. At a high level, the processes below make up vulnerability management—each with its own subprocesses and tasks.
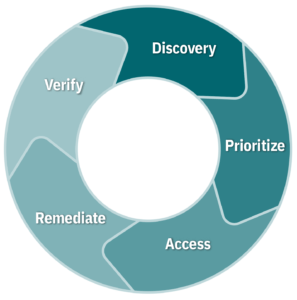
- Discovery: You can’t secure what you’re unaware of. The first step of vulnerability management is to take an inventory of all your digital assets such as endpoints, servers, IPs, applications, and operating systems. This will help you identify and prioritize the weakest facets of your digital infrastructure. Discovery should be performed regularly on an automated schedule including:
-
- Threat and vulnerability updates.
- External scans.
- Internal vulnerability scans.
- Penetration testing.
- Prioritize: Discovered assets need to be categorized into groups and assigned a risk-based prioritization based on criticality to the organization.
- Assess: Establishing a risk baseline for your point of reference is important as vulnerabilities are remediated and risk is eliminated. Assessments provide an ongoing baseline over time and give your organization insight into which vulnerabilities to prioritize.
- Remediate: Based on risk prioritization, vulnerabilities should be remediated through patching or reconfiguration. Your team needs to understand that vulnerabilities and threats require different remediation responses depending on the types. Software vulnerabilities can be patched and reconfigured to reduce risk.
- Verify: Validation of remediation is accomplished through additional scans and/or IT reporting.
Finally, reporting is a critical component to include in your vulnerability management program. Key stakeholders like IT, executives, and the C-suite all need to understand the current state of risk around vulnerabilities and tactical recommendations on how vulnerabilities need to be addressed.
- Reviewing and producing tactical reporting on vulnerabilities identified and remediated will help security teams stay up to date on the latest vulnerabilities and health of your ecosystem.
- Executives need a summary of the current state of vulnerability. A weekly report of common CVEs and threats can help your security team fine-tune systems, whereas a monthly external and quarterly internal report can give more insight into the types of vulnerabilities that were identified and remediated.
- The C-suite needs high-level reporting such as simple risk assessment reports across your list of inventoried assets. These reports are critical to provide a high-level view of the value vulnerability management brings to the business.
A strong vulnerability management program is a continual life cycle of identifying, categorizing, prioritizing, and remediating vulnerabilities across the entire organization. Human error and misconfigurations continue to be leading causes of data breaches. In fact, 16% of data breaches in 2020 were caused by vulnerabilities in third-party software, while 19% of data breaches were caused by cloud misconfigurations, highlighting the value of having a comprehensive vulnerability management program.2
For organizations that need an effective vulnerability management program, Pondurance offers Pondurance VMP, a comprehensive vulnerability management service that continually identifies, categorizes, prioritizes, and helps resolve vulnerabilities. We enable you to stay confident that vulnerabilities are promptly discovered and remediated, protecting you from attackers looking to exploit these vulnerabilities, without placing a burden on your internal staff. Learn more about VMP.
Sources:
- Research reveals increase in critical, low complexity vulnerabilities, SecurityBrief, Feb 2021.
- Cost of a Data Breach Report 2021, IBM, 2021.
