Ransomware-as-a-Service (RaaS), DarkSide, and the Colonial Pipeline
Pondurance May 13, 2021
The Cybersecurity & Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) confirmed this week that DarkSide, a ransomware as a service organization, is responsible for the Colonial Pipeline attack. As of May 12, the cyberattack caused the Colonial Pipeline to shut down, causing gas shortages affecting 45% of the fuel consumed on the East Coast. As of Tuesday, governors in North Carolina, Georgia, and Virginia declared states of emergency and took steps to relax fuel transport rules to ease the price increases at gas stations. The pipeline has resumed operations, but it will take several days for gas to reach its final destination to return to normal operations.
DarkSide has apologized for this attack, stating on its website that it does not “participate in geopolitics” and should not be tied “with a defined government and [to] look for other motives.” However, the damage from the ransomware as a service (RaaS) organization is already done.
DarkSide operates as a RaaS organization servicing multiple clusters of sub-operators that it calls affiliates. These affiliates benefit from ready-to-use ransomware tools that enable them to carry out more attacks and increase the number of successful ransomware payouts.
The cyberattacks carried out by DarkSide all follow relatively the same playbook of tools and tactics as other ransomware groups. Through our hundreds of incident response engagements, we were able to view how the DarkSide works by exfiltrating data, moving laterally, and deploying ransomware. The attackers focus on encrypting ESXi servers, a type-1 hypervisor developed by VMware. A hypervisor is a software that runs and manages virtual machines (VMs). Other ransomware groups have encrypted VMs in the past but are encrypting them at the operating system level — the same way that a regular Windows laptop or server would be encrypted. The DarkSide cyberattacks take the encryption a step further to the ESXi servers, which render the VMs unusable or unbootable.
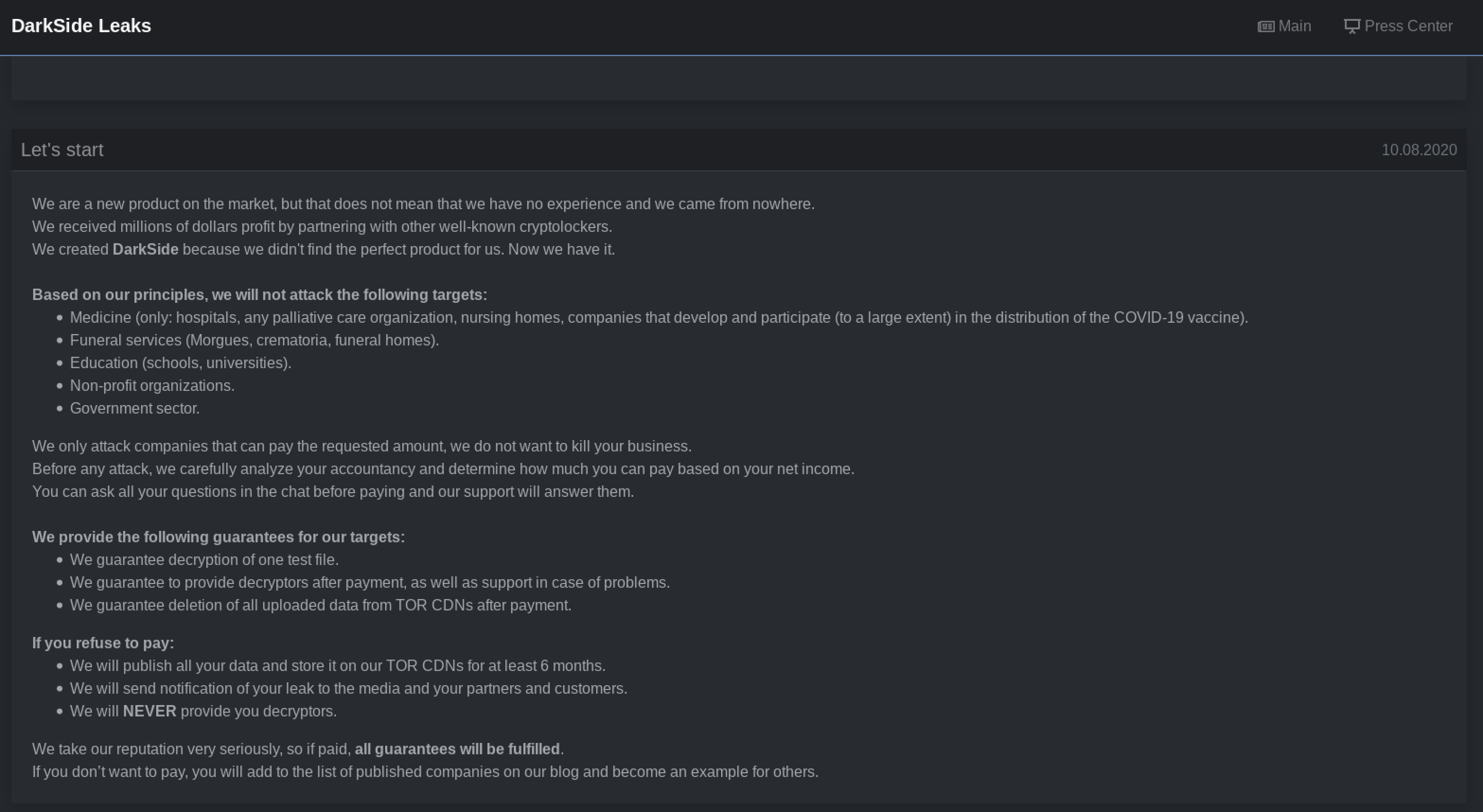
In the recent Colonial Pipeline attack, cybercriminals used DarkSide to gain access to the victim’s network to encrypt and exfiltrate data, holding the data for ransom and threatening to expose it if the victim does not pay the ransom. Since its start in August 2020, DarkSide has targeted organizations in manufacturing, legal, insurance, healthcare, and energy, even though its dark web blog page says that it will not attack targets in medicine, funeral services, education, nonprofit organizations, or the government sector. If a victim is not able to pay, DarkSide will “publish all of your data and store it” on TOR CDNs for at least six months and promote it to partners for purchase. Unfortunately, the number of victims has increased since August 2020, with the overall growth showing that more affiliates are using ransomware as a service.
Overall, ransomware has increased 62% globally since 2019 and 158% in North America alone. The growth can be attributed to a few areas:
- Ransomware provides optionality for attackers. Once an attacker has both exfiltrated and encrypted the data of interest, they can offer to unlock the data—or threaten to release it publicly if the ransom is not paid.
- Ransomware has a proven business model with a lack of consequences, depending on where the attackers geographically reside.
- Ransomware can be delivered via multiple different vectors of compromise so no one product or solution solves for ransomware. Without comprehensive visibility, defense, and response capabilities, it is difficult to protect against ransomware.
- Perpetrators are often paid by cyber insurance carriers so they somehow feel they are not hurting the organization (i.e., hospitals, small businesses, etc.).
Prevention is always the most effective defense against ransomware. It is key to maintain cybersecurity hygiene including ongoing strategic approaches for defense in depth, enhanced auditing verbosity, and continuous monitoring of deployed technologies. For full mitigation recommendations, please refer to the CISA best practices.
As illustrated with the evolution of ransomware as a service techniques, tools are not enough to stop motivated attackers. Cyberattacks are carried out by humans, and they are getting smarter and more creative. As long as there are human attackers, you will need human defenders to ensure your organization is safe from a cyberattack. Human expertise, like that of a managed detection and response (MDR) team, is needed to detect and take action on threats and vulnerabilities before bad actors can do real damage. Learn more about MDR in our webinar Demystifying MDR for the Security Conscious Buyer.
