Modern Problems Require Modern Solutions – The SMB Path to Comprehensive Cybersecurity
Pondurance July 29, 2022
This digital world we live in can be a real jungle sometimes. Companies and individuals consume and produce more data each day, heck every second, than our minds can even fathom. And bad actors are trying to gain access or prevent you from gaining access to that data, creating costly and sometimes catastrophic problems. The digital attack surface is so broad and the cost of breaches so devastating that no one can treat cybersecurity as an afterthought.
There was a time where cyberattacks mostly targeted large enterprises, but as we all know, that is no longer the case. Not only that, the techniques and technologies hackers use today are becoming increasingly more sophisticated, and it’s harder than ever to maintain a cybersecurity posture that protects you on all fronts.
I was recently the victim of a cyberattack that I can admit was pretty impressive. Someone was able to put a fraudulent charge on my credit card by making it look like one of my kids had made a purchase on an online game she frequently plays and makes purchases in. I was able to flag that threat and help my daughter change her password, but the next day a similar charge appeared on my credit card statement. Only this time, it was made to look like my other kid had purchased something in a game he always plays. At this point, I realized a more complicated game was afoot. It appeared someone had attained information from one family member and was using it to infiltrate other accounts. It also appeared they were planning to play the long game, making very small, incremental charges that appeared to be normal spending by my kids. If I were not so maniacal about my finances, this could have continued unnoticed for a long time!
Smash cut to me, the family IT guy, frantically trying to change and document every password associated with every account for every family member. So. Many. PASSWORDS! It took hours. And I’m just one guy, with one credit card, who only got hit for less than $20.
Imagine being in that situation, only now it’s your job with millions of dollars and your entire reputation at stake. This is the reality for many IT and cybersecurity pros working in small and medium-size businesses (SMBs) today. Many of the challenges they face in trying to stay protected, things like a lack of expertise or 24/7 coverage, are the same challenges that led to my own situation. But these can’t be solved by changing a few passwords.
Skilled attackers, complex environments, and resource constraints – it’s all too much
Pondurance recently commissioned a study from Forrester Consulting to explore how SMBs are evolving their cybersecurity operations practices to protect their organizations and the people they serve. Part 1 of this blog series discusses some of the findings in Attackers Don’t Sleep, But Your Employees Need To as they relate to where SMBs are along the path to cybersecurity maturity. What I want to focus on here are the findings surfaced by the study that illuminate the truly monumental challenges these organizations face.
As the study notes, “Business leaders should no longer ask, ‘Could this happen to our organization?’ because yes — it most certainly can.” Indeed. Seventy-five percent of respondents indicated that they have seen an increase in cyberattacks over the last three years. And, eerily, these organizations are experiencing similar challenges to the ones I was facing in my own life, only on a much larger, more critical scale!
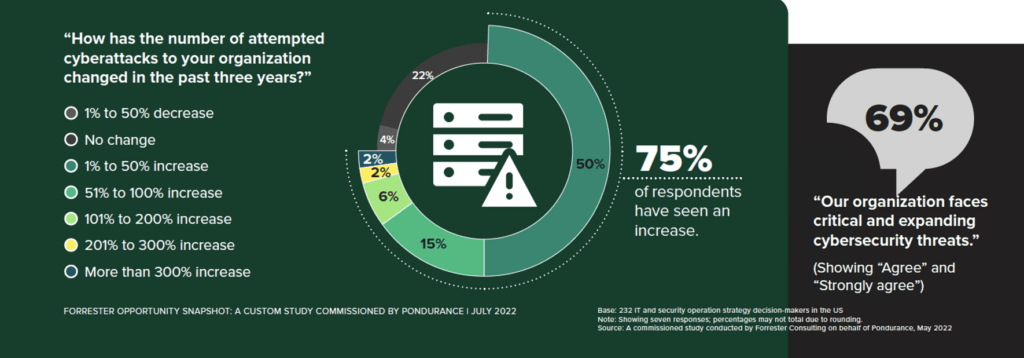
Let’s take a look at the biggest issues facing the SMBs that Forrester Consulting polled for this study as they try to maintain protection from cyberthreats:
- 57% doesn’t have 24/7 security operations coverage
- 42% lacks the skills and expertise necessary to maintain a strong security posture
- 38% notes an increase in attacker sophistication as a major challenge
- 36% struggles to provide employees with the right security tools
The study also notes that SMBs struggle with detection and response to endpoint, network, and cloud-based threats. The risk is compounded by the fact that many significantly lack the resources, expertise, and general bandwidth to focus on strategic activities like developing plans and playbooks and conducting thorough post-breach investigations. Worst of all, many of them are not even monitoring their environments around-the-clock. SMBs aren’t quite as bad off as a guy changing all his passwords in the middle of the night, but this is a little too close for comfort.
Insufficient resourcing is a critical gap
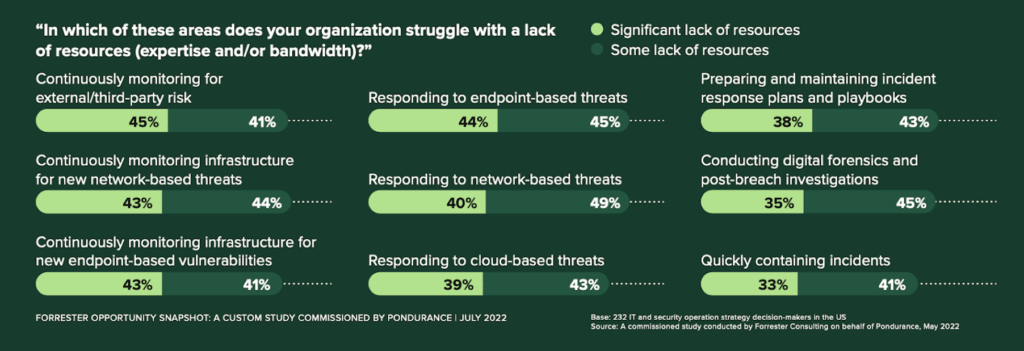
Attackers Don’t Sleep, But Your Employees Need To study sheds light on the most difficult to overcome cybersecurity challenges facing SMBs today and indicates that lack of resources and expertise is quite possibly the most critical of them all. When asked, “In which of these areas does your organization struggle with lack of resources (expertise and/or bandwidth)?,” the majority of respondents identified either a significant or at least some lack of resources committed to continuous monitoring and response capabilities for external third-party risks, network-based threats, and endpoint-based vulnerabilities. Not only that, the majority also indicated that lack of resources is preventing them from maintaining incident response plans, conducting digital forensics, and even containing incidents quickly. Those are some major vulnerabilities being left to chance with short-staffed teams!
This is why, naturally, the respondents report spending 60% of their cybersecurity operations budgets on managed and consulting services. It’s clear that many SMBs need a partner to ensure around-the-clock monitoring and incident response, not to mention help maturing their cybersecurity posture.
Where do SMBs go from here?
Knowing you need help is only half the battle. With so many choices in the managed detection and response (MDR) and managed security services space, it’s imperative that SMBs select the right provider for their specific needs. Pondurance not only delivers every service on that SMB “wish list” with a combination of best-in-class technology, 24/7 coverage, and some of the best cybersecurity talent in the industry but does so with an emphasis on collaboration and communication with clients. Pondurance’s high-touch approach and commitment to defending the human experience have proven to be successful for clients looking to shore up their security posture and evolve with the ever-changing threat landscape.
Stay tuned as we dive deeper into more of the findings from Attackers Don’t Sleep, But Your Employees Need To report here at the Pondurance blog, and please join us for an enlightening webinar with Lyndon Brown, Chief Strategy Officer with Pondurance, and guest speaker Jeff Pollard, Vice President, Principal Analyst with Forrester Consulting, as they discuss the findings of this Forrester Consulting study and provide guidance for achieving the 24/7 security operations center coverage required to help SMBs respond to cyber threats.
