“Oh, No You Don’t!” How To Recognize and Prevent a Spear-Phishing Attack
William Gadzinski April 07, 2022
In this day and age, even the most tech-illiterate have heard about the threat of phishing emails and have learned to be wary of emails promising vast foreign riches to those who wire money. While the would-be victims have learned, however, so too have the perpetrators of these omnipresent phishing scams. Nowadays, phishing scams are sophisticated, and can fool even the wariest users if their guard is let down for even a minute.
Turning a numbers game into a targeted phishing expedition
Running a phishing scam is a numbers game. You take the number of emails sent and divide it by the percentage of successful phishes and you get your yield. For some scammers, the best way to up their yield has been to simply send more emails. Even with a dramatically low success rate, one can still rake in the cash by ensuring everyone who would fall for a scam gets an email, and the tiny cost of engaging in a spam campaign certainly supports that. However, a clever scammer will realize that instead of taking the shotgun approach, it may be better to cut the cash out of someone’s pocket with a scalpel. These attackers use a more targeted approach known as spear-phishing, a technique designed to boost the likelihood of a successful phishing expedition.
While almost all phishing emails will introduce a sense of urgency to prompt a quick, sometimes thoughtless reaction, spear-phishing introduces a certain level of personalization to the emails to help bypass the initial sniff test. Scammers will include details like names, dates, and job positions to add to the apparent legitimacy of an otherwise scam email. Spear-phishing works by introducing certain information to establish an elevated level of trust, causing the victims to let their guard down.
Social profiles, recent events, and company announcements leave helpful clues
There are plenty of ways that a scammer can gather the information needed to conduct a spear-phishing attack. Attackers can glean a lot of information about people from their social media, where users may post more information about their lives than they realize. For instance, a social media post about a new car may prompt a scammer to send a fake manufacturer email regarding “an important safety recall.” Another example involves targeting various employees of a company, especially those whose professional profile (LinkedIn) states they work in a valuable role, such as finance.
In another example, recent events or announcements by a company may prompt subsequent emails, like the following email that occurred after a company’s remote work policy was announced:
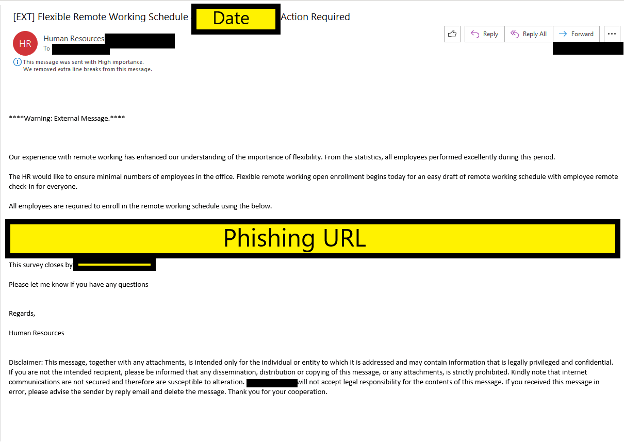
Spear phishing email regarding phony “Remote Work Schedule”
Beware the botnet
While the timing and tailoring of phishing emails often suggest a certain level of manual interaction, some threat groups are known to include automated spear-phishing activity in their malicious payloads. The well-known “QakBot” (or “QBot”) botnet uses a different technique wherein upon installation the malware will exfiltrate emails from the affected system. The botnet then injects fake replies within email threads, and a victim who is having an ongoing conversation may not notice the change in sender address. The following example from a recent incident shows how one infected system can inject a malicious reply into an otherwise benign conversation, spear-phishing the victim by hijacking the already established trust between the two parties.
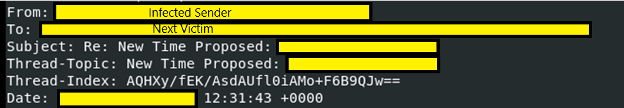
In the subject line of the QBot email, note the Re:, indicating this was sent as a reply to an existing thread.
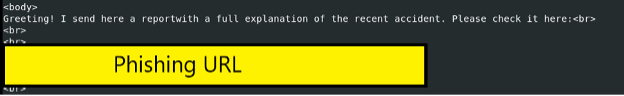
The body of this QBot email includes the URL to a malicious installer. This is one method QBot uses to self-propagate.
Spear-phishing’s ultimate goal is generally to gain access to a system or account, and spear-phishing emails often contain URLs or hyperlinks that lead to malicious web forms intended to steal credentials or include malicious attachments designed to download and execute malware on the victim’s system. With the access gained by the initial spear-phish the attacker can mount a ransomware attack on a network, steal confidential information, or steal banking information.
The whaling attack
The final, most sophisticated form of spear-phishing is known as “whaling,” in which an attacker performs meticulous research to target one specific person, typically an executive or high-ranking official. The perpetrator of a whaling attack will generally attempt the attack to gain access to an executive’s email, what’s known as a business email compromise. These attacks typically leverage the email access to accomplish some form of wire fraud by “authorizing” a change in automated clearing house information and can last for months, with the attacker using their access to hide the evidence of the fraud until the money is no longer recoverable.
Recommendations for combating spear-phishing
Spear-phishing represents one of the most common threats to IT security currently, and is a technique used by APTs, nation-states, and run-of-the-mill scammers alike. To operate securely, an organization must recognize this and plan accordingly. Some recommendations for an organization looking to combat the threat of spear-phishing are:
- Implement email security best practices such as Sender Policy Framework (SPF) and DomainKeys Identified Mail checking, and ensure the relevant email filtering policies are restrictive enough to block malicious emails.
- Implement email URL filtering through a security vendor to prevent employees from falling victim to known phishing sites.
- Restrict and scan email attachments, only allowing attachments which are necessary for business operations.
- Implement continued education policies regarding phishing and perform phishing exercises with employees to simulate various types of phishing emails.
Be safe out there. The waters can be treacherous.
Additional resources:
