Pondurance Uncovers Conti Ransomware Group Capitalizing on Microsoft Exchange Vulnerabilities
Pondurance August 11, 2021
The Pondurance research team recently uncovered that the Conti ransomware group is now obtaining access to environments stemming from the Hafnium exploits that occurred back in February and March 2021 within Microsoft Exchange. These zero-day vulnerabilities could affect hundreds of thousands of systems. Microsoft shared that “in the three weeks after the Microsoft Exchange server vulnerabilities were disclosed and the security updates were released, Microsoft saw numerous other attackers adopting the exploit into their toolkits. Attackers are known to rapidly work to reverse engineer patches and develop exploits.”1
Our team identified that an on-premise Microsoft Exchange server still had web shells installed that stemmed from the Hafnium vulnerability back in late February and early March 2021. Pondurance also identified that the Hafnium exploitation chain resulted in the installation of an unauthorized and abused remote monitoring and management (RMM) agent. The unauthorized RMM tool remained present on the victim machine for approximately four months and granted the ability for remote interaction with the victim machine. In July, the RMM tool was utilized by outside actors to install additional malicious frameworks, including Cobalt Strike. The resulting actions concluded with the installation of Conti ransomware.
Although Microsoft issued patches and diagnostics following the initial February exploit, organizations likely patched these systems without performing due diligence, and systems are still compromised.
While the victim organization was aware of the Microsoft Exchange vulnerabilities and took mitigation actions within its response, the organization did not identify the already installed backdoor access on the affected system. As a result, unauthorized access remained beyond the patching of the affected system.
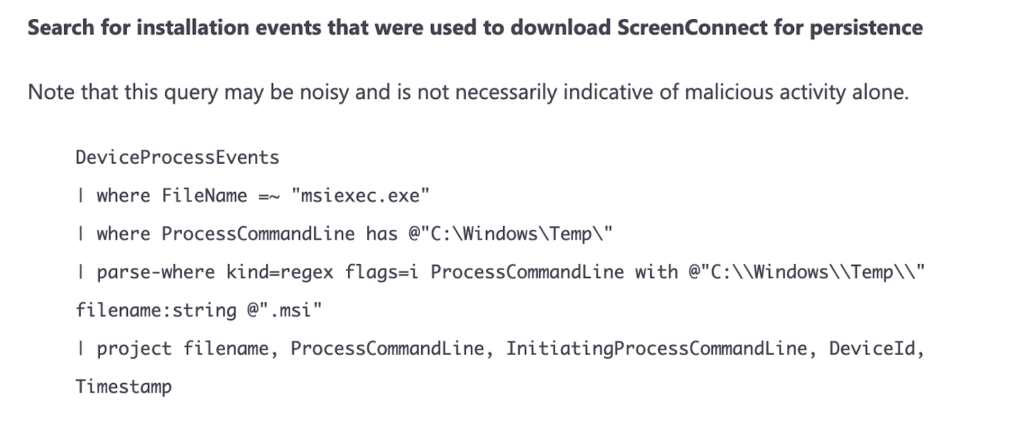
Despite patching, thousands of devices might still be compromised. Pondurance recommends searching for unauthorized ScreenConnect services installed on on-premises Microsoft Exchange servers that were vulnerable to Hafnium at some point. These services should be present within the registry and would have generated “Service Created” event logs (event ID 7045) at the time of install in March 2021. You may also find ScreenConnect-related folders created in the file system under C:\ProgramData\, C:\Program Files (x86)\, and C:\Windows\Temp\.
In late March, Microsoft released an article containing indicators of compromise, which included mentions of ScreenConnect abuse:1
Implementing a vulnerability management program is critical to quickly identify and remediate these types of vulnerabilities before they become breaches. Common areas to assess for risks range from operation systems, applications, cloud infrastructure, and servers.
Vulnerability management is continual and requires an initial inventory of all assets that will be scanned externally and internally. These scans can help you prioritize risk throughout your organization if you are scanning at least once a month.
Scanning more frequently will give your organization greater visibility and reduce the cost associated with incident response recovery. Today’s security tools can help you simplify and automate vulnerability management. Understanding the vulnerability and patching or reconfiguring is key to being proactive in protecting your digital assets.
For organizations that need an effective vulnerability management program, we offer Pondurance VMP, a comprehensive vulnerability management service that continually identifies, categorizes, prioritizes and helps resolve vulnerabilities. We enable you to stay confident that vulnerabilities are promptly discovered and remediated, protecting you from attackers looking to exploit these vulnerabilities, without placing a burden on your internal staff.
Learn more about Pondurance VMP.
Source:
- Analyzing attacks taking advantage of the Exchange Server vulnerabilities, Microsoft, Mar 25, 2021.
