Our mission is to ensure that your organization is able to detect and respond to cyber threats — regardless of size, industry, or current in-house capabilities. Our advanced platform combined with decades of human intelligence decrease risk to your mission. We combine our advanced platform with decades of human intelligence to decrease risk to your mission.
Managed Detection and Response
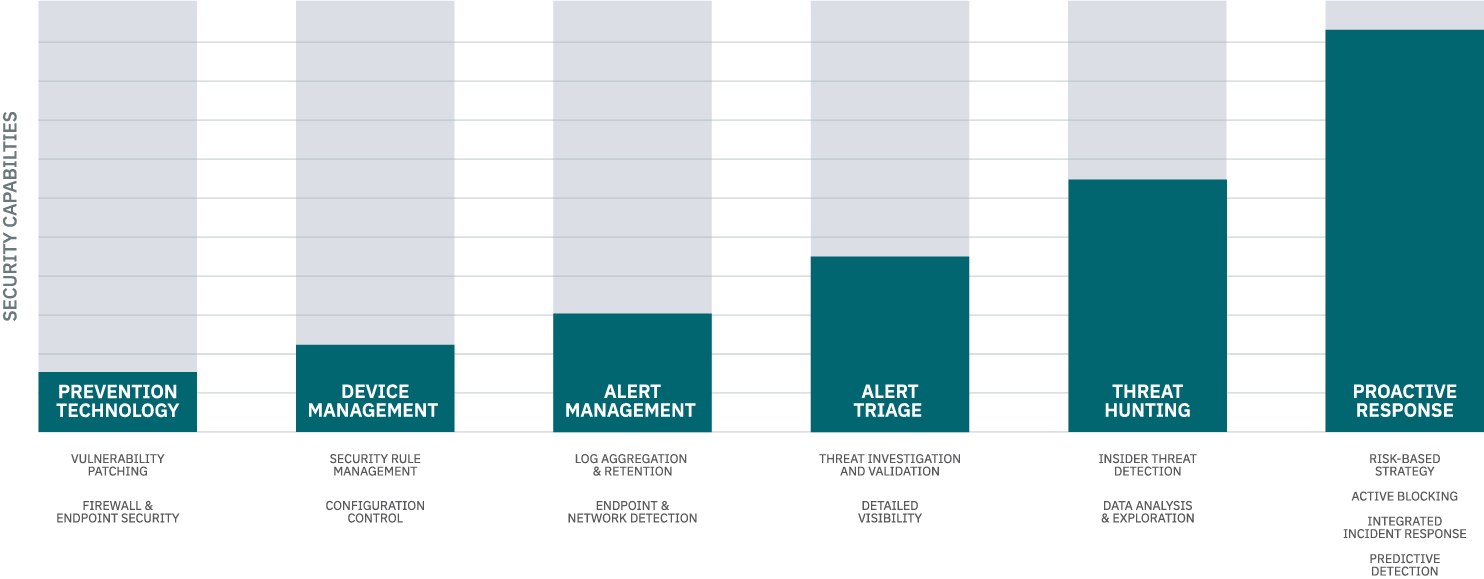
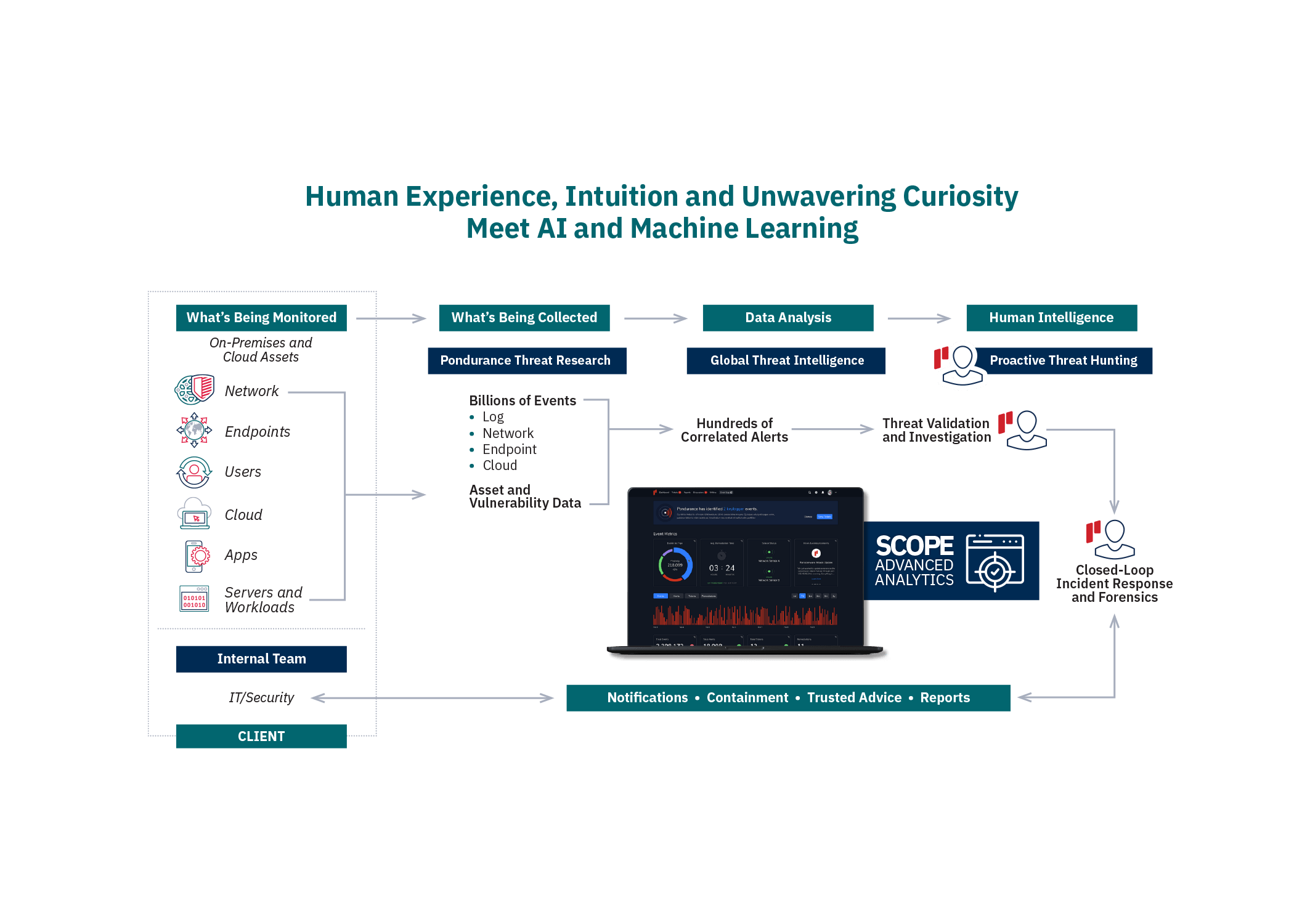
Recognized by Gartner, Pondurance provides 24/7 U.S.-based SOC services powered by analysts, threat hunters, and incident responders who utilize our advanced cloud-native platform to provide you with continuous cyber risk reduction. By integrating 360-degree visibility across network, log, endpoint, and cloud data and with proactive threat hunting, we reduce the time it takes you to respond to emerging cyber threats.
Pondurance MDR is the proactive security service backed by authentic human intelligence. Technology is not enough to stop cyber threats. Human attackers must be confronted by human defenders.